Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How we can extract Windows Event description inste...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How we can extract Windows Event description instead of Raw data which only give info of Event ID?
How we can extract Windows Event description instead of Raw data which only give info of Event ID..Is it possible to extract exact event info..
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ahh, the (in)famous windows events 😉
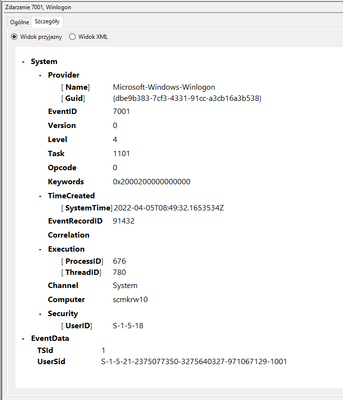
It's a tricky beast to handle. In general, windows event consists of several well-structured fields (that's what you get in the "System" part of the event), some EventData part which varies between different kinds of events and that's it. It's well structured, it can be ingested by TA-windows as either "old" format or XML. And that's pretty much all there is in the event itself. You can see it in the "details" tab in event viewer.
If you'd use any other popular log retrieving mechanics (like rsyslog windows agent, kiwi syslog server or any other such solution), you'd also only get that data.
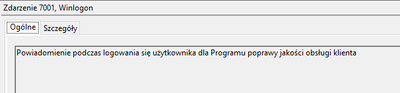
I suppose what you're referring to as "Event description" is the rendition of the event data in the eventviewer which means this (this is the same event):
Unfortunately, that's not stored anywhere in the event itself and is not easily queryable from the event log.
It's a rendition of specific event done by eventviewer using registered DLL libraries according to the event properties. The description is not contained within the event itself (as you can see on the first screenshot).
Which makes sense since - for example - text descriptions may vary between language versions of windows whereas the raw event data is still the same - it's still Event 7001 regardless of whether it's displayed in English, Polish, Japanese or whatever other language Windows supports.
If you somehow managed to be able to render the event data into the "description" text as you call it, you'd still have to make your own script/program to pull the data from the event log and push it somehow to splunk. There is no ready-made solution for this. And there is a good reason - as I said before - the event codes and identifiers are constant across all installations and you're looking for EventID 4672 you're looking for the same action regardless of what language your windows uses. Imagine creating a search that would work on any language version of windows log if it was to search by the text representation of this event. That would be ridiculous.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the reply..
I mean exact event info as below instead of RAW data which got no info which can be understand..
Event 1069 : Cluster resource '%1' in clustered role '%2' failed.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @afraanajam,
you should ask this to Microsoft!
Anyway, this is the wineventlog format and it isn't possible (for my knoledge) to take them in a different format.
You could preparse the windows logs using a script but it's a very hard work!
The only thing that you can do (and I hint because I did it many times) to reduce license consuption ingesting WinEventLogs is to discard some unuseful events because there are many events like those!
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Splunk is extracting the windows event logs but its presenting in RAW format which is not readable except the useful info is event id..
My question was instead of RAW data which splunk understandable language, can we extract exact event details from server..
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @afraanajam,
what do you mean with "Windows Event description"?
I think that Windows Event Logs are much verbose.
If you want to reduce the license consuption, you could filter your data filtering (before indexing) your data taking only the relevant for you data and discarding the others (for more details see at https://docs.splunk.com/Documentation/Splunk/8.2.5/Forwarding/Routeandfilterdatad), or you could also delete a not relevant part of each event taking only thge relevant parts (for more details see at https://docs.splunk.com/Documentation/Splunk/8.2.5/Data/Anonymizedata).
Ciao.
Giuseppe