Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Search
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to write search with CASE and MATCH function?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to write search with CASE and MATCH function?
syazwani
Path Finder
04-21-2022
02:12 AM
Hi peeps,
I need help to fine tune this query;
index=network sourcetype=ping
| eval pingsuccess=case(match(ping_status, "succeeded"), Number)
Basically, I want to create a new field for ping success that will show the event count as values.
Please help.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
gcusello

SplunkTrust
04-21-2022
02:19 AM
Hi @syazwani,
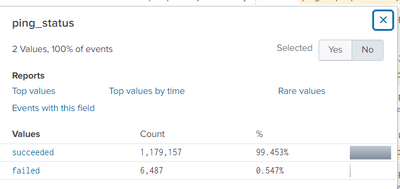
let me understand: what are the values of ping_status?
if they are only "succeded" and "failed", you don't need anything:
index=network sourcetype=ping
| stats count BY ping_statusif you have more values for ping_status that you want to aggregate you could use if or case functions:
index=network sourcetype=ping
| eval pingsuccess=if(ping_status="succeeded"), "succeeded","failed")
| stats count BY pingsuccessCiao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
syazwani
Path Finder
04-21-2022
02:24 AM
Thank you for your reply. I want to create a base search for ITSI KPI configuration. That's why I need it to be extracted and create a single field for it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
gcusello

SplunkTrust
04-21-2022
02:28 AM
Hi @syazwani,
using my hint are you able to create the field?
otherwise, could you describe some sample of the values of the ping_status field?
Ciao.
Giuseppe
Get Updates on the Splunk Community!
Introducing the Splunk Community Dashboard Challenge!
Welcome to Splunk Community Dashboard Challenge! This is your chance to showcase your skills in creating ...
Wondering How to Build Resiliency in the Cloud?
IT leaders are choosing Splunk Cloud as an ideal cloud transformation platform to drive business resilience, ...
Updated Data Management and AWS GDI Inventory in Splunk Observability
We’re making some changes to Data Management and Infrastructure Inventory for AWS. The Data Management page, ...