- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to use Splunk AND command to find field 3?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
++EXT-ID[05] FLD[Wallet Provider Device..] FRMT[TLV] LL[1] LEN[32] DATA[4AD74D9421FE60B5688EF727F1BC7488] ++EXT-ID[06] FLD[Wallet Provider Accoun..] FRMT[TLV] LL[1] LEN[32] DATA[4AD74D9421FE60B5688EF727F1BC7488] ++EXT-ID[07] FLD[Wallet Provider Reason..] FRMT[TLV] LL[1] LEN[32] DATA[30DA9557329255041D0B5FC268651435]
I wanted to identify the list where FLD[Wallet Provider Device..] and FLD[Wallet Provider Accoun..] are present but FLD[Wallet Provider Reason..] is missing
In the above examples all three fields are present. I wanted to identify Field 1, Field 2 received but field 3 is missing
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @jayeshrajvir,
good for you, see next time!
If my answer solves your requirement, please, accept it for the other people of Community..
Ciao and happy splunking.
Giuseppe
P.S.: Karma Points are appreciated by all the Contributors;-)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
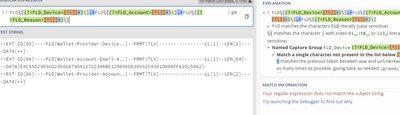
Do you mean something like this?
(?<wallet_provider>FLD\[Wallet Provider Device\.\.\]).+? (?<wallet_account>FLD\[Wallet Account Email A\.\.\]).+?(?!FLD\[Wallet Provider Reason\.\.\])- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i tried but no matching condition
Test String
++EXT-ID[05] FLD[Wallet Provider Device..] FRMT[TLV] LL[1] LEN[2] DATA[**]
++EXT-ID[0A] FLD[Wallet Account Email A..] FRMT[TLV] LL[1] LEN[64] DATA[E4C55D23036D23E668790A1272C3AABE129096D830532C4301D000FFA2D15062]
++EXT-ID[06] FLD[Wallet Provider Accoun..] FRMT[TLV] LL[1] LEN[2] DATA[**]
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @jayeshrajvir,
let me understand: the test string is one event or more events?
My regex is for one event, if you have a row for each event, you have to use a different regex and the only way to understand if the field is FLD[Wallet Provider Device..] or FLD[Wallet Provider Accoun..] or FLD[Wallet Provider Reason..] it could be the format of the field, could you share some sample for your three fields?
I'm interested only on the format, e.g. \w\w\w\d\d\d\w\w or \w+\@\w+\.\w+
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
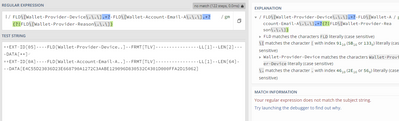
Hi @jayeshrajvir,
could you try this regex?
| rex "FLD\[(?<FLD_Device>[^\]]+)\].*FLD\[(?<FLD_Account>[^\]]+)\].*FLD\[(?<FLD_Reason>[^\]]+)\]"that you can test at https://regex101.com/r/qXNk4U/1
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello
.* would match everything, basically 1st condition
https://regex101.com/r/qXNk4U/1
I have a logs where
1. the fields highlighted in both blue and red present,
2. only fields highlighted in blue present and
3. field highlighted in red present
I wanted to fetch transactions log where it should fetch fields highlighted in blue is present and field highlighted in red is not present
+EXT-ID[02] FLD[02 Wallet Provider] FRMT[LLVAR-TLV-Group..] LL[2] LEN[40] DATA[??????????????????????????????????]
++EXT-ID[05] FLD[Wallet Provider Device..] FRMT[TLV] LL[1] LEN[2] DATA[**]
++EXT-ID[06] FLD[Wallet Provider Accoun..] FRMT[TLV] LL[1] LEN[2] DATA[**]
++EXT-ID[07] FLD[Wallet Provider Reason..] FRMT[TLV] LL[1] LEN[64] DATA[5BAAE330347FC58AC794FA535144DAD88440BDF0515AD3B0AE374A7975B612DB]
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you try my suggestion? Here in a regex command to filter for only the events which match the criteria
| regex _raw="FLD\[Wallet Provider Device\.\.\].+? FLD\[Wallet Account Email A\.\.\].+?(?!FLD\[Wallet Provider Reason\.\.\])"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is not working because you have split your event into two lines - try it without the linebreak in the middle
If your events do actually have linebreaks in them, then try adding (?ms) to start of the regex
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @ITWhisperer
Thanks for your support and time. Its working as expected. Much appreciated.
Regards,
Jayesh
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please can you mark the response which contains the solution you used as the solution so that others with similar questions might benefit?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @jayeshrajvir,
as I said, is there a predefined format for FLD[Wallet Provider Device..], FLD[Wallet Provider Accoun..] and FLD[Wallet Provider Reason..]?
If yes, could you share some sample of the three fields?
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
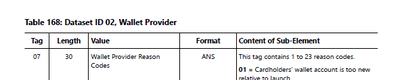
Hi @gcusello
This is the pre-defined format, Device Score and Account Score if present then length will be 2 bytes, Wallet Provider Reason is 32 bytes fixed. Please see below.
Kindly let me know if additional info is required.
++EXT-ID[05] FLD[Wallet Provider Device..] FRMT[TLV] LL[1] LEN[2] DATA[**]
++EXT-ID[06] FLD[Wallet Provider Accoun..] FRMT[TLV] LL[1] LEN[2] DATA[**]
++EXT-ID[07] FLD[Wallet Provider Reason..] FRMT[TLV] LL[1] LEN[32] DATA[792194208EDDB782F97EC3C2ACD7FB99]
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @jayeshrajvir,
I need of a sample of the three fields so I can create the regexes for the extraction, e.g. Device_Score and Account_Score if present have a length of 2 bytes, but what's the format?
I can suppose that being they a score they will always have the format of two digits, is it correct?
Wallet_Provider_Reason has a lenght of 32 bytes, does it means that it always have 32 chars? can these chars be only digits or also letter or also alphanumeric?
what's the format of Wallet_Provider_Device?
It's the first time that you say that you need to extract also Device_Score and Account_Score, so what's you need?
The problem is that we cannot use the string before square brackets to identify fields, so the only way (if possible) is the format and other eventual rules that are in your logs.
I need these information to create the regexes.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello
Please find the format below - Wallet Provider Device Score and Account Score Numeric 02 bytes
whereas Wallet Provider Reason code variable length Alpha Numeric. Hope this helps!!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @jayeshrajvir,
let me understand: is the EXT-ID a fixed value?
in other words, is [05] always before the Device_Score and [06] always before Account_Score and [07] before Reason?
if yes you could use three regexes like these:
| rex "EXT\-ID\[05\]\s+FLD\[(?<Device_Score>\d*\d*)
| rex "EXT\-ID\[06\]\s+FLD\[(?<Account_Score>\d*\d*)
| rex "EXT\-ID\[07\]\s+FLD\[(?<Reason>[^\]*)Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello
Many thanks for your support and patience.
Yes 05 Device Score always logged prior to 06 Account Score.
Regards,
Jayesh
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @jayeshrajvir,
good for you, see next time!
If my answer solves your requirement, please, accept it for the other people of Community..
Ciao and happy splunking.
Giuseppe
P.S.: Karma Points are appreciated by all the Contributors;-)