- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to use MV expand to extract a data grouped by ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to use MV expand to extract a data grouped by itself?
Hi splunk community
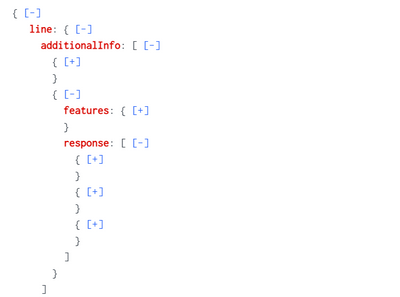
I am currently trying to break up a log. It is in this format after converting to a json
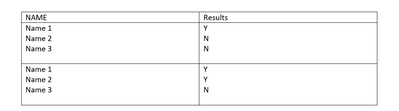
Each plus under response has a block of information with several variables. I need splunk to pull out the values of the variables i tell it to but grouped together. I tried breaking this up using MV expand but when I do it groups up the names in one log and the results which make it difficult to graph. an example of how it looks is below. the below format doesnt work since every name variable will have the same output when graphed because every single group is one "log" which makes insights difficult.
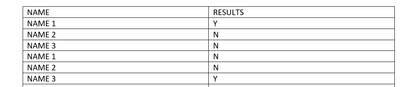
I need it to do something like this
the search that i have been using is below
index=myindex attrs.deploymentKey="production" "MY COPY" "MY ROUTER*"
| spath input=line
| tojson auto(line)
| spath path=line.additionalInfo{}
| eval resp=mvindex('line.additionalInfo{}', 0,2)
| mvexpand data
| spath input=data output=my_name path=response{}.NAME
| spath input=data output=my_results path=response{}.Results
| where my_results = "Y"
| table my_name, my_results
. any help would be much appreciated
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
in my opinion, you're doing wayyy too much work. let splunk do the work. i love how i see people forcing all these things when splunk has amazing abilities if you'll just let it. i can help you.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can help you finish this. you should reach out to me.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@splunkjas1 how would you go about solving this then?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Spunk_user89
It very hard to help without the the raw event data. Can you please provide an example of the raw event using the Insert/Edit code sample button so any event formatting in protected.
Obfuscate or remove any sensitive data.
Doing this will greatly help anyone that is looking to provide a solution for you.