Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to search if data contain value from the other...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to search if data contain value from the other fields?
Hi
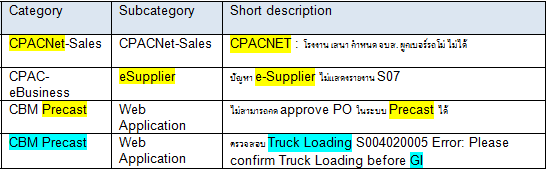
I'm very new in Splunk, I'd like to find the event where the short description contain the "Category" or "Subcategory field. (Example in the the yellow highlight.
Other than the field value, how can I match the related words between the fields?
For example,
"CBM Precast" related to "Truck loading" and "GI"
If the Splunk found "Truck loading" or"GI", it also mean that this event match with "Category" field as well.
Please help!!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi urapaveerapan,
you have to create a simple search like the following:
if you want a value that fully matches the Category field
index=your_index sourcetype=your_sourcetype Category="CBM Precast" | ...
if you want a value that partially matches the Category field
index=your_index sourcetype=your_sourcetype Category="*Precast*" | ...
or if you're not sure of the field to use in search
index=your_index sourcetype=your_sourcetype Precast | ...
Beware that the field name is case sensitive, instead field value isn't.
I suggest to follow the search tutorial that you can find at http://docs.splunk.com/Documentation/Splunk/6.6.0/SearchTutorial/WelcometotheSearchTutorial
Bye.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Giuseppe,
The search item is dynamic. It depend on the value in Category or Subcategory fields. So I cannot fill the extact word in its.
Let say, if it is sql query, it gonna be like
select * from [table_name] where [short description] like '%'||Category||'%' or [short description] like '%'||Subcategory||'%'
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi urapaveerapan,
you can try to use
Category="*short_description*" OR Subategory="*short_description*"
Or try using the like option (see at http://docs.splunk.com/Documentation/Splunk/6.6.0/SearchReference/ConditionalFunctions)
... | where like(Category, "%short_description%") OR like(Subcategory, "%short_description%")
Obviously this search will be not so quick!
Bye.
Giuseppe