- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to replace the similar uri_paths in a Splunk s...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to replace the similar uri_paths in a Splunk search to calculate the response time for each endpoint?
Example:
application="example" index=web uri_path="/some/example/*"
In my application, I have similar uri_paths. I want to replace uri_path and calculate the response time for each endpoint.
Uri_paths: I have 4 different uri_paths, each one of uri_path has different number on the end, that number are nothing but a uniqu generated number for each request.
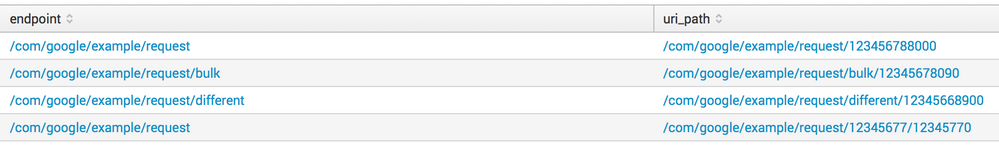
/com/google/example/request/123456788000
/com/google/example/request/98760456098
/com/google/example/request/4521346098
/com/google/example/request/6983256709
/com/google/example/request/45321670987
/com/google/example/request/9834708641
/com/google/example/request/bulk/12345678090
/com/google/example/request/bulk/6521340976
/com/google/example/request/bulk/5679084124
/com/google/example/request/bulk/428429720
/com/google/example/request/bulk/7267311890
/com/google/example/request/bulk/254102157
/com/google/example/request/different/12345668900
/com/google/example/request/different/6358097421
/com/google/example/request/different/0789043267
/com/google/example/request/different/67562463129
/com/google/example/request/different/0737912913243
/com/google/example/request/12345677/12345770
/com/google/example/request/126938710/2397100701
/com/google/example/request/625197012804/77064261381
/com/google/example/request/26912783-12/07129512
/com/google/example/request/6877207401/09737861
So i would like to consider the each end point into one uri_path and want to caliculate the response time of that uri_path. In this way, i ll get to know, how long each endpoint is taking to complete the process.
How to replace above similar uri_path into separate uri_path to calculate the response time of each endpoint?
I have replaced some uri_paths using replace command, for above request it is not working.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry but I'm struggling to understand what you are trying to do.
If you just want to get rid of the random number at the end of the uri_path so that you can then group by endpoint, then the following should work. If you please provide some information on the desired output.
| rex field=uri_path "(?<endpoint>.+?)/[\d/]+$"
Example:
Regards,
J
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Instead of replace, try rex. Here is an example. I'm unsure where you're getting the {ID} from...
rex mode=sed field=uri_path "s/(com\/google\/example\/request\/).*/\1{ID}/g"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This will give you the last two segments of uri_path
*UPDATED*
... | rex field=uri_path "(?<endpoint>.+?)/[\d/]+$" | stats earliest(_time) as start latest(_time) as end by endpoint | eval duration=tostring(round(end-start, 0), "duration")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@greeshmak try my updated answer. If that does work, please share desired output and an example of what you call "endpoint"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you give an example of how the replaced value might look?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm replacing the uri_path by using the replace command.
Ex:
application="example" index="web" uri_path="/some/example/*"| replace "/com/google/example/request/*" WITH "/com/google/example/request/{ID}" in uri_path|replace "/com/google/example/request/bulk/*" with "/com/google/example/request/bulk/{Id}" in uri_path| replace "/com/google/example/request/different/*" with "/com/google/example/request/different/{Id}" in uri_path| replace " /com/google/example/request/*/*" with " /com/google/example/request/{Id1}/{Id2}"
Results are only showing the "/com/google/example/request/*" end point since I'm using the * after request.