Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to populate a column that generates time diffe...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to populate a column that generates time difference for the results which are generated from a stats command?
pkhedwal
New Member
05-14-2018
02:52 AM
I have this query.
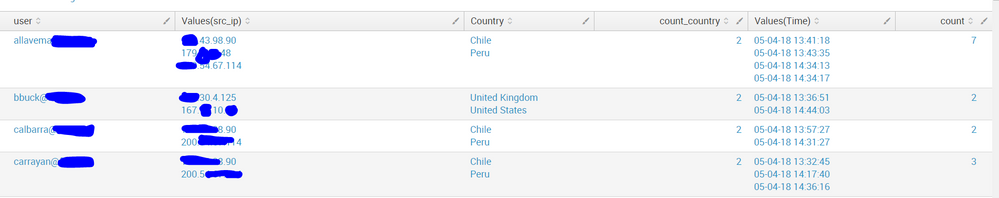
index=azure Operation=UserLoggedIn user!=Unknown|sort - _time | iplocation ClientIP | eval Time=strftime(_time, "%m-%d-%y %H:%M:%S") | stats Values(src_ip), values(Country) as Country, dc(Country) as count_country, Values(Time) count by user | where count_country>1
Results are:
Now I want to calculate the time difference between 1st and last time which are present in the column Values(Time).
I want a column to be populated right after this column.
Any help?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Richfez

SplunkTrust
05-14-2018
04:58 AM
You could give this a try.
index=azure Operation=UserLoggedIn user!=Unknown|
| iplocation ClientIP | eval Time=strftime(_time, "%m-%d-%y %H:%M:%S")
| stats Values(src_ip), values(Country) as Country, latest(_time) AS earlyTime, earliest(_time) AS lateTime, dc(Country) as count_country, Values(Time) count by user
| eval elapsedSeconds = tostring(lateTime - earlyTime, "duration") | where count_country>1
We add in the two fields you need (earliest and latest time) into the stats, then do a little math and format the results.
Give that a try, and let us know how it works!
-Rich
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
martin_mueller

SplunkTrust
05-14-2018
04:57 AM
First off, remove the sort command - it contributes nothing to your result, and causes only the first 10000 rows to be considered.
If _time and Time are identical, you can add range(_time) as range to your stats to get the difference.
Get Updates on the Splunk Community!
Stay Connected: Your Guide to November Tech Talks, Office Hours, and Webinars!
What are Community Office Hours?
Community Office Hours is an interactive 60-minute Zoom series where ...
Index This | When is October more than just the tenth month?
October 2025 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with this ...
Observe and Secure All Apps with Splunk
Join Us for Our Next Tech Talk: Observe and Secure All Apps with SplunkAs organizations continue to innovate ...