Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to get the count of the field whose value is g...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to get the count of the field whose value is greater than 0 ?
I have logs in Splunk which has a field named Message as Highligthed below
Date = 2019-04-09 11:43:20,946 | Level = INFO | RequestID = (null) | ErrorCode = (null) | ErrorMessage = Records details | Alert = false | Message = Manufacture:Actia;Total Records:20;Processed Records:18;Failed Records:2
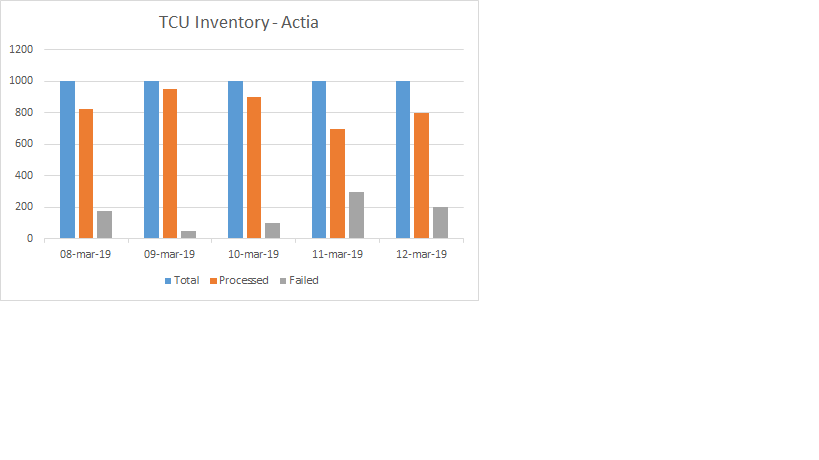
I need to extract Manufacture name , total records, processed records and failed records values and get the count of the records and display it in Bar chart
Below is the query which i tried to generate the result
index ="XYZ" "Failed Records" "Manufacture:Actia" |rex field=_raw "Total Records:(?\d+);Processed Records:(?\d+);Failed Records:(?\d+)" | timechart count(total) as Total, count(processed) as processed,count(failed) as Failed
i need to get the count for the records
Total Records :20
Processed records : 18
Failed Records: 2
Please suggest.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Step 1: get your field extractions straight globally for this sourcetype (so you don't need to do the rex). Try this:
index ="XYZ" AND sourcetype="SomeSourcetypeHere" AND "Failed Records" AND "Manufacture:Actia"
| rex "Total Records:\s*(?<TotalRecords>\d+);\s*Processed Records:\s*(?<ProcessedRecords>\d+);\s*Failed Records:\s*(?<FailedRecords>\d+)"
| timechart count AS EventCount, sum(TotalRecords) AS Total, sum(ProcessedRecords) AS Processed, sum(FailedRecords) AS Failed
Possibly, depending on how your events are generated (what they mean), you might need max instead of sum.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| makeresults
| eval _raw="Date = 2019-04-09 11:43:20,946 | Level = INFO | RequestID = | ErrorCode = | ErrorMessage = Records details | Alert = false | Message = Manufacture:Actia;Total Records:20;Processed Records:18;Failed Records:2"
| extract pairdelim="|;" kvdelim="=:"
| eval _time=strptime(replace(Date,",","."),"%F %T.%3Q")
Hi, folks.
For structured logs, try extract.
Regex-free.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
if the info in the message is a result a running process and you want to get the latest status you can use latest(*) instead of count. e.g. | timechart latest(total) as Total latest(processed) as processed latest(failed) as Failed
Count doesn't seam to make much sense to me in that context, but I might by assuming something wrong. Can you give more details about the context that log is generated?
Hope I was able to help you. If so, some karma would be appreciated.