Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to generate a table where the values of my "se...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
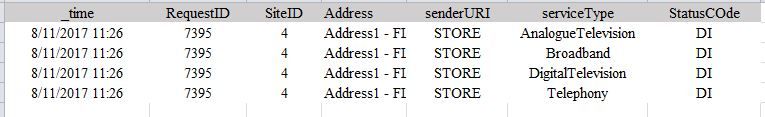
Below is the example of single request with multiple lines where ServiceType is different.
Required result to be as below, where Service type is placed into single row with different field names
Happy to take any other suggestions. Thanks in advance
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well in your sample output, the field name is same and will not work. If output like below is acceptable, try the query.
OUTPUT
_time, RequestID SiteID Address senderURI serviceType StatusCode
xxx yyy xxx ppp qqqq AnalogueTelevision,Broadband,..othervalues.. statuscodevalue
Query
..your current search | stats values(serviceType) as serviceType by _time, RequestID SiteID Address senderURI StatusCode | nomv serviceType
OR
OUTPUT
_time, RequestID SiteID Address senderURI AnalogueTelevision Broadband DigitalTelevision Telephony StatusCode
xxx yyy xxx ppp qqqq yes yes yes yes statuscodevalue
Query
..your current search | eval temp=_time."#".RequestID."#".SiteID."##".Address."#".senderURI."#".StatusCode | stats count over temp by serviceType | rex field=temp "(?<time>\d+)#(?<RequestID>[^#]+)#(?<SiteID>[^#]+)#(?<Address>[^#]+)#(?<senderURI>[^#]+)#(?<StatusCode>[^#]+)" | fields - temp | rename time as _time| table _time, RequestID SiteID Address senderURI * StatusCode
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well in your sample output, the field name is same and will not work. If output like below is acceptable, try the query.
OUTPUT
_time, RequestID SiteID Address senderURI serviceType StatusCode
xxx yyy xxx ppp qqqq AnalogueTelevision,Broadband,..othervalues.. statuscodevalue
Query
..your current search | stats values(serviceType) as serviceType by _time, RequestID SiteID Address senderURI StatusCode | nomv serviceType
OR
OUTPUT
_time, RequestID SiteID Address senderURI AnalogueTelevision Broadband DigitalTelevision Telephony StatusCode
xxx yyy xxx ppp qqqq yes yes yes yes statuscodevalue
Query
..your current search | eval temp=_time."#".RequestID."#".SiteID."##".Address."#".senderURI."#".StatusCode | stats count over temp by serviceType | rex field=temp "(?<time>\d+)#(?<RequestID>[^#]+)#(?<SiteID>[^#]+)#(?<Address>[^#]+)#(?<senderURI>[^#]+)#(?<StatusCode>[^#]+)" | fields - temp | rename time as _time| table _time, RequestID SiteID Address senderURI * StatusCode
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks for your fast reply.
Apologies for not mentioning before, what will be the query if new field name of "serviceType" is to be displayed for every serviceType value. Something like below.
servicetype1 servicetype2 servicetype3 servicetype4
xxx yyy zzz www