Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to extract info from nested data with specific...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
paulito
Explorer
04-13-2022
10:53 AM
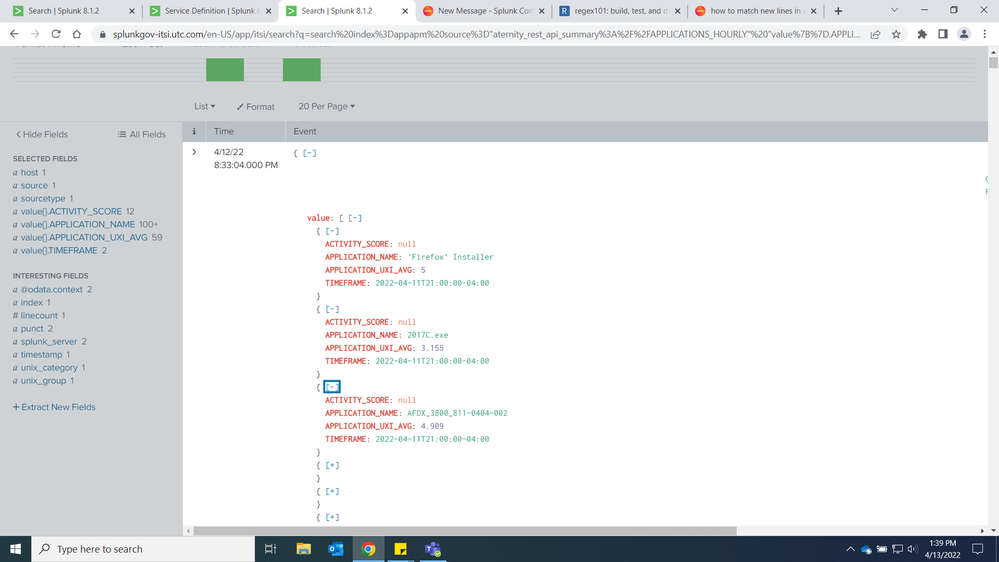
I need to extract the Activity Score and Application UXI Average but only when the Application Name is a certain name.
It's a weird one for me because of the way data comes in. As you can see each event has multiple application names, activity scores, uxi averages and timeframes. So even when I specify for a certain app in a search, since the app name is in an event, I get the whole event which includes all the other apps and metrics.
I hope what I'm explaining is clear and any help would be appreciated.
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ITWhisperer

SplunkTrust
04-13-2022
11:45 AM
| spath value{} output=value
| mvexpand value
| spath input=value
| where APPLICATION_NAME="certain app"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ITWhisperer

SplunkTrust
04-13-2022
11:45 AM
| spath value{} output=value
| mvexpand value
| spath input=value
| where APPLICATION_NAME="certain app"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
paulito
Explorer
04-13-2022
12:23 PM
Works perfectly, thank you!
Get Updates on the Splunk Community!
Enterprise Security (ES) Essentials 8.3 is Now GA — Smarter Detections, Faster ...
As of today, Enterprise Security (ES) Essentials 8.3 is now generally available, helping SOC teams simplify ...
AI for AppInspect
We’re excited to announce two new updates to AppInspect designed to save you time and make the app approval ...
App Platform's 2025 Year in Review: A Year of Innovation, Growth, and Community
As we step into 2026, it’s the perfect moment to reflect on what an extraordinary year 2025 was for the Splunk ...