Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to extract an integer value after colon and di...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to extract an integer value after colon and display results using timechart?
NOTICE: <script>: [3473090307|3167225225](SENDER[10.65.197.2:5073]): Current Active Inbound Calls: NOTICE: <script>: [3218481898|03116204181](SENDER[192.168.15.11:7060]): Current Active Inbound Calls: 8
I want to extract the integer value after the colon (:) i.e. 0 and 8 and then display these results as timechart.
I'm writing it as:
host=Kamailio NON=Active
| eval totalCount=mvcount(NON)
| timechart span=300s count by totalCount
p.s: NON is a field with multiple other values and Active is one of them which contains those integers which I want to display.
Any degree of help would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did that manually, using the + Extract New Fields (ss attached):
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
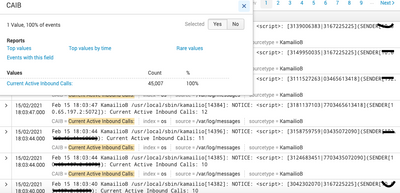
If you have already extracted CAIB, what values do you have in the field?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As you can see, the value you have in CAIB is "Current Active Inbound Calls:" which is why the rex does not find any numbers when you specify field CAIB, and why the rex without specifying the field (which will work on _raw) does find the values you are after.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It Is not overly clear what you events look like or which part of the event you are trying to extract. However, assuming it is a number after "Calls: " then this might help
| rex "Calls: {?<calls>\d+)"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, thanks for the reply.
To answer your question, it is indeed a number after the " Calls: "
I tried this solution but it does seem to search from the entire event and not from what I've typed in the search string:
CAIB="Current Active Inbound Calls:" | rex field=CAIB ".*=(?<number>\d+)\D" | timechart span=30s count by max(number)
where CAIB is a field that I extracted myself and number is a variable I used to store the values
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How have you extracted CAIB?