Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: help to display 0 if no results
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello
as you can see i stats events following the bin time value
But when the bin time value is equal to 0, I have nothing displayed
I would like to display the results even if the result is 0 but just for hour corresponding to the current hour or to the previous hour
It means that I dont want to display 0 for a bin time which is later than the current hour
index=toto sourcetype=titi
| bin span=1h _time
| eval time = strftime(_time, "%H:%M")
| stats count as Pb by s time
| search Pb >= 3
| stats dc(s) as nbs by time
| rename time as Heure
I tried like this but it doesnt works
| appendpipe
[ stats count as _events
| where _events = 0
| eval nbs = 0 ]
could you help please?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please clarify what you mean by "no results" - do you mean that there are no events left in the pipeline (in which case the appendpipe technique should work) or that some time points have no results and you want a zero displayed for these timepoints?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
that some time points have no results and I want a zero displayed for these timepoints...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Use timechart; for this you will need to move the eval time further down the search
index=toto sourcetype=titi
| bin span=1h _time
| stats count as Pb by s _time
| search Pb >= 3
| timechart dc(s) as nbs span=1h
| eval time = strftime(_time, "%H:%M")
| stats sum(nbs) as nbs by time
| rename time as Heure- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
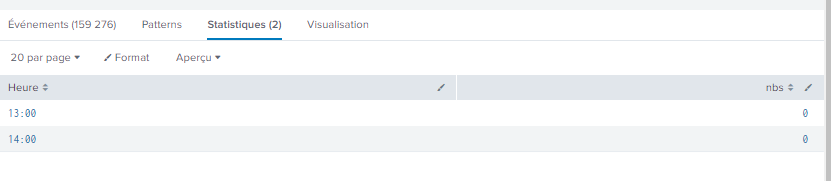
correct but what I dont like with this is that it displays _time which didn't occured
for example I displays 14h, 15, 16h with 0 result but I would like to display 0 results only for previous hour than current hour
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This seems like a different ask from the original post. Please can you be more specific as the what you are trying to achieve, and what you have already tried?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have updated my post
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index=toto sourcetype=titi earliest=-1h@h
| bin span=1h _time
| stats count as Pb by s _time
| search Pb >= 3
| timechart dc(s) as nbs span=1h
| eval time = strftime(_time, "%H:%M")
| stats sum(nbs) as nbs by time
| rename time as Heure- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
it's exactly the same problem
With this, I just have 1h events and not previous events
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you set earliest to -1h@h how are you getting results for more than an hour ago?
Can you show the search you are using for these results?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just have this
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Which is what you amended your question to ask for, i.e. current and previous hour even if the counts are 0?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
no
my search calculate events on the slot time below
earliest=@d+7h latest=@d+19h so I want to display all the events following this slot time with the bin span
| bin span=1h _timeso it works perfectly except when the results is 0
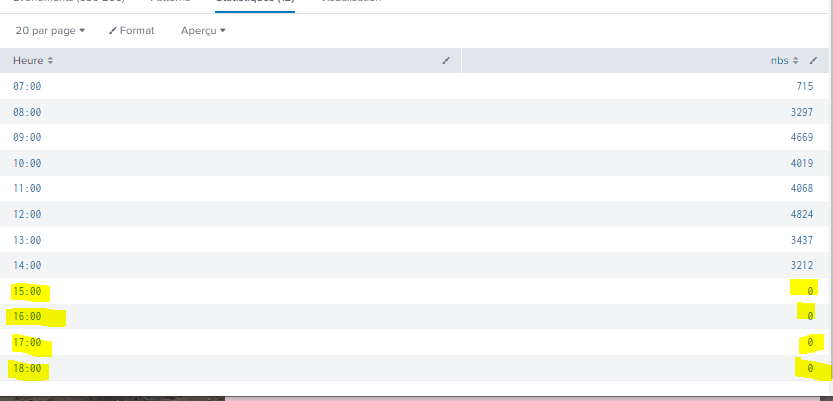
If it's 0, actually nothing is displayed
So I need to display results = 0 if the bin time is previous to the current time but not if the bin time exceed the current time
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Finally, some clarity 😀
index=toto sourcetype=titi earliest=@d+7h latest=@d+19h
| bin span=1h _time
| stats count as Pb by s _time
| search Pb >= 3
| timechart dc(s) as nbs span=1h
| where _time < now()
| eval time = strftime(_time, "%H:%M")
| stats sum(nbs) as nbs by time
| rename time as Heure- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks