Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to create a regex for a log file which contain...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to create a regex for a log file which contains multiple values throughout the log which required same field name?
Hello Team,
This is the first time I am posting a question and hope that I have explained it thoroughly.
I am trying to create a regex for a log file which contains multiple values throughout the log which required same field name. but splunk does not allows to use same field name again.
Here is the sample log:
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
Note: Text values are 4 char and Number contains 10 digits.
How can I move forward to achieve a field extraction and format like this?
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
Thank You in Advance 😊
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am not sure what you mean by "Splunk does not allow to use the same field name again." (This is SPL, of course anything is possible®😃)
Because your field values are separated by a known, fixed string "/TXT1/TXT2", a literal solution would be
| eval samefield = split(_raw, "/TXT1/TXT2")
| eval samefield = mvfilter(len(samefield) != 0)
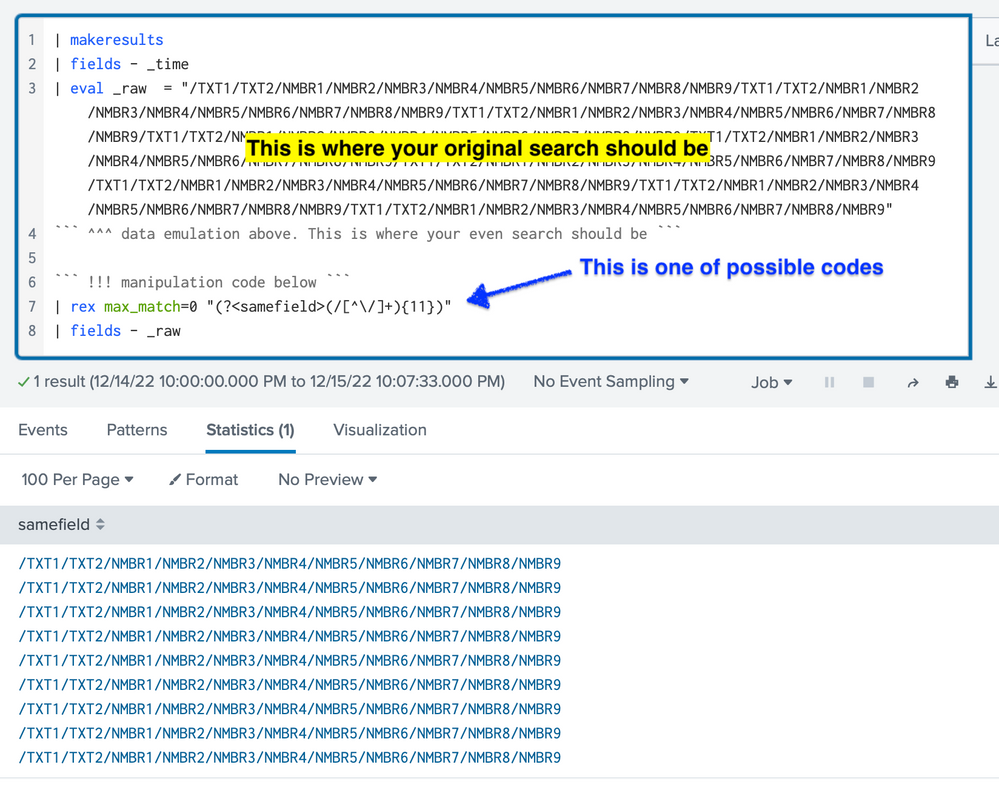
| eval samefield = mvmap(samefield, "/TXT1/TXT2" . samefield)This is an emulation I used to test the above; you can play with it and compare with real data
| makeresults
| eval _raw = "/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9"
``` data emulation above ```There can be several variants based on fixed text values.
If you want to relax the condition that the text portion is known and fixed, you can use the text and number characteristics you described,
| rex max_match=0 "(?<samefield>(/\w{4}){2}(/d{3}){9})"You can even generalize this to only require a total of 11 path segments:
| rex max_match=0 "(?<samefield>(/[^\/]+){11})"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
the provided sample is a single log and is not separated by fields, but I want to implement fields with the help of regex in this format.
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9
/TXT1/TXT2/NMBR1/NMBR2/NMBR3/NMBR4/NMBR5/NMBR6/NMBR7/NMBR8/NMBR9- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@mssoni Have you tried my code? Yes, I do understand that's one string and that's what I emulated: One very long string.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not yet, I am really confused how to place this in the query, this is the first time I am working on its front end,
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
really confused how to place this in the query
One way to help others help you unconfuse you is to illustrate the SPL you have at hand (simplify and anonymize as needed), then explain what confuses you, what error you get, or why the result is not what you wanted.
I already explained how I test my sample codes based on your sample data and description of your requirements. I assume that you know where the search window is. Just paste data emulation code above the manipulation code, and you can review the results. Like this:
(In this example, I used the shorted code.) Does this look like what you need? Then, just replace the data emulation part with your own event search.
Hope this helps.