Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to create a correlation search based on data p...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Kitag345
Explorer
02-17-2023
09:27 AM
Hello,
I would like to request guidance on how to create a correlation search based on data provided by SANS Threat Intelligence from https://isc.sans.edu/block.txt
The malicious IPs from "block.txt" are updated regularly. How can my correlation search track that change in real-time? What queries to use?
Notes: The SANS Threat Intel has already been enabled.
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
nyc_jason

Splunk Employee
02-17-2023
09:43 AM
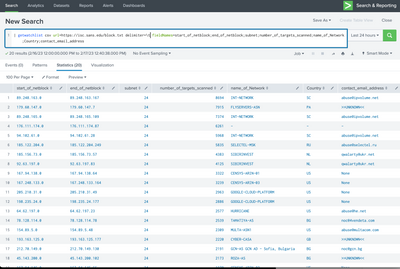
consider using the PAVO Getwatchlist add-on, then you can do this:
Or for performance, schedule the search every 30min, and pipe it to a lookup. then run your search using the lookup for matches.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
nyc_jason

Splunk Employee
02-17-2023
09:43 AM
consider using the PAVO Getwatchlist add-on, then you can do this:
Or for performance, schedule the search every 30min, and pipe it to a lookup. then run your search using the lookup for matches.
Get Updates on the Splunk Community!
September Community Champions: A Shoutout to Our Contributors!
As we close the books on another fantastic month, we want to take a moment to celebrate the people who are the ...
Splunk Decoded: Service Maps vs Service Analyzer Tree View vs Flow Maps
It’s Monday morning, and your phone is buzzing with alert escalations – your customer-facing portal is running ...
What’s New in Splunk Observability – September 2025
What's NewWe are excited to announce the latest enhancements to Splunk Observability, designed to help ITOps ...