Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to convert `_time` to the column and `host` ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
microsac
Explorer
03-31-2022
05:08 AM
How to convert `_time` to the column and `host` as an index while using `mstats`?
| mstats avg(_value) prestats=true WHERE metric_name="cpu.*" AND index="*" AND
(host="host01.example.com" OR
host="host02.example.com" OR
host="host03.example.com" OR
host="host04.example.com" OR
host="host05.example.com" OR
host="host06.example.com"
) AND `sai_metrics_indexes` span=auto BY metric_name
| timechart avg(_value) as "Avg" span=30m by metric_name
| fillnull value=0
| foreach *[| eval "<<FIELD>>"=round('<<FIELD>>',2)]
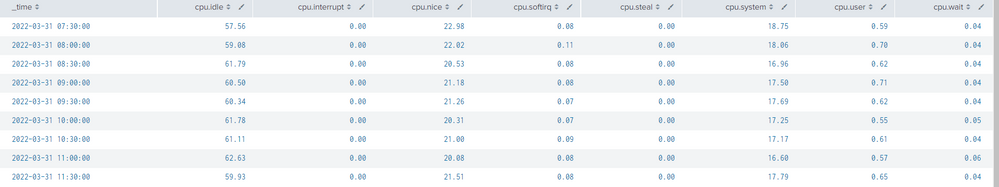
The above results in as follows:
What is Desired:
host _time cpu.idle cpu.interrupt cpu.nice cpu.softirq cpu.steal cpu.system cpu.user cpu.wait
host01.example.com 2022-03-31 07:30:00 57.56 0.00 22.98 0.08 0.00 18.75 0.59 0.04
host01.example.com 2022-03-31 08:00:00 59.08 0.00 22.02 0.11 0.00 18.06 0.70 0.04
host01.example.com 2022-03-31 08:00:00 61.79 0.00 20.53 0.08 0.00 16.96 0.62 0.04
Any help will be uch appeciated.
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
somesoni2
Revered Legend
03-31-2022
11:43 AM
## Since timechart only support group by one field, we're using this alternative implementation. Doing bucket of _time with same span that was used in timechart##
| bucket span=30m _time
## Merging two fields, so that charting can be done for two fields.
| eval temp=host."##"._time
## Running chart with merge field appearing as rows and metric_name values are column.
| chart avg(_value) as "Avg" over temp by metric_name
| fillnull value=0
| foreach cpu.* [| eval "<<FIELD>>"=round('<<FIELD>>',2)]
## Getting those merged field back.
| eval host=mvindex(split(temp,"##"),0)
| eval _time=tonumber(mvindex(split(temp,"##"),1))
| fields - temp | table host _time *- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
microsac
Explorer
03-31-2022
08:23 PM
| eval host=mvindex(split(temp,"##"),0) <-- Can you please explain this ?
| eval _time=tonumber(mvindex(split(temp,"##"),1)) <-- Can you please explain this ?
| fields - temp | table host _time *
What is the meaning of using "##", does it has a special meaning here?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
dhirendra761
Contributor
03-31-2022
07:51 AM
You haven't use host in SPL.
Try to use host filed in your SPL first either in stats or BY.
in last
|table host _time *- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
microsac
Explorer
03-31-2022
08:23 AM
@dhirendra761 i tried that in the last line of search but did not list the host, it shows the host column but do not print the hostname's .. it turns blank.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
somesoni2
Revered Legend
03-31-2022
07:45 AM
Give this a try
| mstats avg(_value) prestats=true WHERE metric_name="cpu.*" AND index="*" AND
(host="host01.example.com" OR
host="host02.example.com" OR
host="host03.example.com" OR
host="host04.example.com" OR
host="host05.example.com" OR
host="host06.example.com"
) AND `sai_metrics_indexes` span=auto BY metric_name host
| bucket span=30m _time
| eval temp=host."##"._time
| chart avg(_value) as "Avg" over temp by metric_name
| fillnull value=0
| foreach cpu.* [| eval "<<FIELD>>"=round('<<FIELD>>',2)]
| eval host=mvindex(split(temp,"##"),0)
| eval _time=tonumber(mvindex(split(temp,"##"),1))
| fields - temp | table host _time *- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
microsac
Explorer
03-31-2022
08:06 AM
@somesoni2 , this works can you explain the part you placed it working that will also help posterity.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
somesoni2
Revered Legend
03-31-2022
11:43 AM
## Since timechart only support group by one field, we're using this alternative implementation. Doing bucket of _time with same span that was used in timechart##
| bucket span=30m _time
## Merging two fields, so that charting can be done for two fields.
| eval temp=host."##"._time
## Running chart with merge field appearing as rows and metric_name values are column.
| chart avg(_value) as "Avg" over temp by metric_name
| fillnull value=0
| foreach cpu.* [| eval "<<FIELD>>"=round('<<FIELD>>',2)]
## Getting those merged field back.
| eval host=mvindex(split(temp,"##"),0)
| eval _time=tonumber(mvindex(split(temp,"##"),1))
| fields - temp | table host _time *
Get Updates on the Splunk Community!
Index This | What is broken 80% of the time by February?
December 2025 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with this ...
Unlock Faster Time-to-Value on Edge and Ingest Processor with New SPL2 Pipeline ...
Hello Splunk Community,
We're thrilled to share an exciting update that will help you manage your data more ...
Splunk MCP & Agentic AI: Machine Data Without Limits
Discover how the Splunk Model Context Protocol (MCP) Server can revolutionize the way your organization uses ...