Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to compare search result for first 15 min and ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to compare search result for first 15 min and last 45 min?
salavilli0611
New Member
09-16-2019
12:00 PM
Following is the result we got
Action_ Name Time Count
ABC 1:15 AM 100
ABC 1:30 AM 200
ABC 1:45 AM 300
ABC 2:00 50
Now I want to compare the row2 (1:30 AM) Count : 200 with row4(2:00 AM) Count 50
I am new to splunk and I don't know how to do it
Following is the below splunk query:
index=... sourcetype= .... | bucket _time span=15m | stats count by Action_Name,_time
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
jacobpevans
Motivator
09-16-2019
01:53 PM
Greetings @salavilli0611,
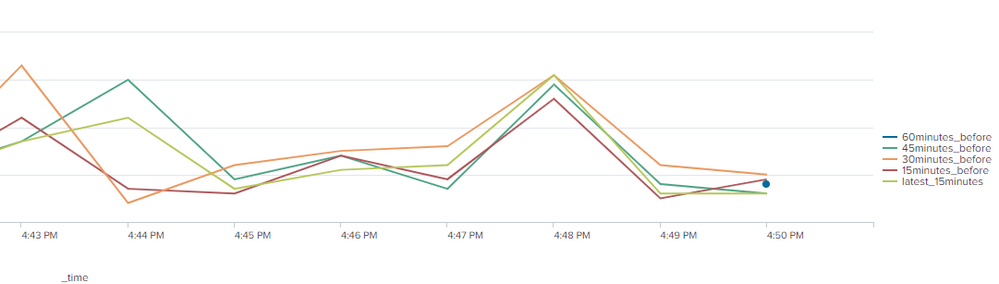
Please take a look at this run-anywhere search. If needed, you can add a by to the timechart, but your sample data does not indicate you do. When you plug this into your search, replace count with sum(count) (and remove the bin command since timechart does that for you)
index=_internal sourcetype=splunkd log_level=ERROR
| timechart span=15m count
| timewrap 15min
Cheers,
Jacob
If you feel this response answered your question, please do not forget to mark it as such. If it did not, but you do have the answer, feel free to answer your own post and accept that as the answer.
Jacob
If you feel this response answered your question, please do not forget to mark it as such. If it did not, but you do have the answer, feel free to answer your own post and accept that as the answer.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
adonio
Ultra Champion
09-16-2019
01:24 PM
what will be the desired result / view / table look like?
Career Survey
First 500 qualified respondents will receive a $20 gift card! Tell us about your professional Splunk journey.
Get Updates on the Splunk Community!
Tech Talk Recap | Mastering Threat Hunting
Mastering Threat HuntingDive into the world of threat hunting, exploring the key differences between ...
Observability for AI Applications: Troubleshooting Latency
If you’re working with proprietary company data, you’re probably going to have a locally hosted LLM or many ...
Splunk AI Assistant for SPL vs. ChatGPT: Which One is Better?
In the age of AI, every tool promises to make our lives easier. From summarizing content to writing code, ...