Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Compare difference in a field from two differe...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to compare difference in a field from two different events?
I am looking to compare two events in same index and sourcetype differentiated by snapshot id's, the main task is to compare the "instance_list" field between latest and last event and send an alert if there is a difference between then as well as display the actual difference.
instance_list field contains the list of instances in a snapshot and i want to compare two events and only display the list of values in that field with is not matching.
Note: Events are in json
Example of instance_list field:
instance_1
instance_2
instance_3
.
.
.
Any help here will be appreciated, thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI @ashvinpandey,
There's probably a more efficient method, but this should get you started:
| gentimes start=-5
``` Generating data starts```
| eval_time=starttime, instance_list="instance_1;instance_2;instance_3;"| streamstats count as id | eval instance_list=if(id=5,"instance_1;instance_2", instance_list) | makemv instance_list delim=";" | makejson output=raw
| rex mode=sed field=raw "s/instance_list\":\s+\"([^\"]+)\"/instance_list\":[\"\1\"]/"
| table raw, _time
| spath input=raw path=instance_list{} output="instance_list"
``` Generate data ends```
``` Get the first and last entries by _time ```
| eventstats max(_time) as oldest, min(_time) as youngest
| where _time=oldest OR _time=youngest
| eval oldest_instance_list=if(_time=oldest,instance_list,null()), youngest_instance_list=if(_time=youngest,instance_list,null())
``` split out the instance_list to see the individual lines ```
| mvexpand instance_list
``` Get the combined instance_lists and times ```
| eventstats values(youngest_instance_list) as youngest_instance_list, values(oldest_instance_list) as oldest_instance_list earliest(_time) as oldest_time, latest(_time) as youngest_time
| stats count, values(youngest_instance_list) as youngest_instance_list, values(oldest_instance_list) as oldest_instance_list, values(oldest_time) as oldest_time, values(youngest_time) as youngest_time by instance_list
``` Any count of 1 means this instance_list was missing from either earliest or latest ```
| search count=1
``` Combine the data to create a good message for the alert ```
| stats values(*) as * by count
| nomv oldest_instance_list | nomv youngest_instance_list | nomv instance_list | eval youngest_time=strftime(youngest_time,"%Y-%m-%d"),oldest_time=strftime(oldest_time,"%Y-%m-%d")
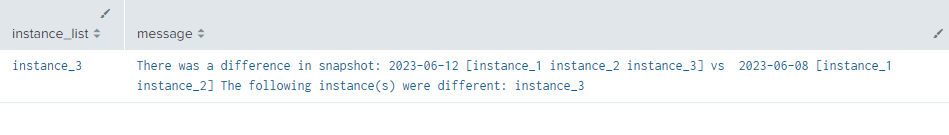
| eval message="There was a difference in snapshot: " + youngest_time + " [" + youngest_instance_list + "] vs " + oldest_time + " [" + oldest_instance_list + "] The following instance(s) were different: " + instance_list
| table instance_list, message
This search creates the json data at the top, then finds any difference between the most recent and oldest events.
E.g. Earliest: instance_, instance_2, instance_3
Latest: instance_1, instance_2
Gives this result:
It gives all the instances that were different, and a message for the alert.
Cheers,
Daniel