Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to combine two searches with streaming command...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I want to combine two search results, whereby I'm only interested in the last x/y events from each subquery. Something like this:
| multisearch
[search index="sli-index"
| eval testtype="endp-health"
| head 3]
[search index="sli-index"
| eval testtype="enp-system"
| head 6]
This leads to following error: ...Error in 'multisearch' command: Multisearch subsearches might only contain purely streaming operations (subsearch 1 contains a non-streaming command)....
Any idea how this can be achieved?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried with append:
index="sli-index"
| eval testtype="endp-health"
| head 1
| append
[search index="sli-index"
| eval testtype="enp-system"
| head 1]But for some reasons I get two events where testtype=="endp-system".
Expected: I get two events: testtype="endp-health" and the other with testtype="endp-system"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Splunk Community,
To combine two search results where you are interested in the last x/y events from each subquery, you can utilize streaming commands effectively by piping the output of the first search into the second one. For instance, you can use command-line tools like grep, awk, or sed to filter and merge the results. If you're dealing with more complex data, consider using a programming language like Python with libraries such as pandas for better manipulation and merging of search results. Finally, to enhance your streaming and searching experience, I recommend you install the Spotify Web Mod PC. This mod can help streamline your music searches and organize your playlists efficiently, providing a seamless integration into your overall workflow.
Best Regards!!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Strange. Works for me.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
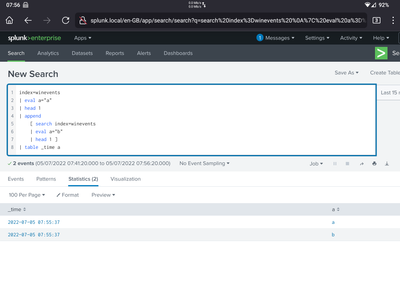
Hi,
after putting the result in a table, the result is OK 🙂
For completeness, this now shows correct results:
index="sli-index"
| eval testtype="endp-health"
| head 3
| append
[search index="sli-index"
| eval testtype="enp-system"
| head 6]
| table _time, testtypeMany Thanks, you saved my day.
Cheers, Martin
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now that's interesting because all comands are streaming. Maybe Splunk tried to optimize the search and came up with some non-streaming equivalent and shot itself in the foot. Anyway. If your subsearches are small and quick you can use append.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried with append:
index="sli-index"
| eval testtype="endp-health"
| head 1
| append
[search index="sli-index"
| eval testtype="enp-system"
| head 1]But for some reasons I get two events where testtype=="endp-system".
Expected: I get two events: testtype="endp-health" and the other with testtype="endp-system"