Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to combine two search results?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to combine two search results?
Hello 🙂
I need your help for a subject.
I want to combine two search results and I need you help beacause I have a problem.
I tried this :
index="nexthink" sourcetype="st_nexthink_device" | append
[| spath "asset.last_boot_duration" output=boot | spath "asset.last_logon_duration" output=logon | spath "asset.name" output=PC | eval demarrage=boot+logon |eval date=strftime(now(),"%d/%m/%Y") |eval annee_now=mvindex(split(date,"/"),-1) | fields demarrage, PC]
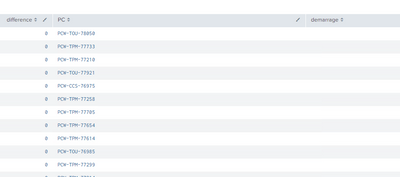
[ |search index=easyvista sourcetype=st_easyvista_generic "Identifiant réseau"="PCW-*" Catégorie="Borne tactile" OR Catégorie="All in One" OR Catégorie="Convertible" OR Catégorie="Odinateurs de bureau" OR Catégorie="Ordinateurs portables" OR Catégorie="Ordinateurs format micro" OR Catégorie="Workstation"
| rename "Identifiant réseau" as PC "Date d'installation" as dd | eval annee=mvindex(split(dd,"/"),-1) | eval date=strftime(now(),"%d/%m/%Y") | eval annee_now=mvindex(split(date,"/"),-1) | eval difference=annee_now-annee |fields difference, PC ] | table difference PC demarrage
But I have a problem with the "demarrage" field.
I can't get it by combining the two searches.
I want to mention that I need :
-> in : index="nexthink" sourcetype="st_nexthink_device" :
-----> asset.last_boot_duration
-----> asset.last_logon_duration
-----> demarrage = BOOT +LOGON
-> in : index=easyvista sourcetype=st_easyvista_generic
-----> date : this year
-----> annee : the year of the installation of the PC
-----> demarrage = BOOT +LOGON
Thank you for your help 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try something like this
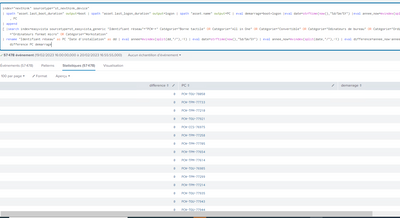
index="nexthink" sourcetype="st_nexthink_device"
| spath "asset.last_boot_duration" output=boot | spath "asset.last_logon_duration" output=logon | spath "asset.name" output=PC | eval demarrage=boot+logon |eval date=strftime(now(),"%d/%m/%Y") |eval annee_now=mvindex(split(date,"/"),-1) | fields demarrage, PC
| append
[ |search index=easyvista sourcetype=st_easyvista_generic "Identifiant réseau"="PCW-*" Catégorie="Borne tactile" OR Catégorie="All in One" OR Catégorie="Convertible" OR Catégorie="Odinateurs de bureau" OR Catégorie="Ordinateurs portables" OR Catégorie="Ordinateurs format micro" OR Catégorie="Workstation"
| rename "Identifiant réseau" as PC "Date d'installation" as dd | eval annee=mvindex(split(dd,"/"),-1) | eval date=strftime(now(),"%d/%m/%Y") | eval annee_now=mvindex(split(date,"/"),-1) | eval difference=annee_now-annee |fields difference, PC ] | table difference PC demarrage- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unfortunately, it doesn't work :
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you share some of your events (particularly from the first search) in a code block </> so that the formatting doesn't hide some of the characters?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The syntax of the event of the search is similar to this :
{"date": 1676910383.7157812, "asset": {"name": "PCW-TOU-74141", "score:Device performance/Boot speed": 0.0, "total_ram": 8589934592, "total_nonsystem_drive_usage": null, "total_nonsystem_drive_capacity": 0, "system_drive_usage": 0.26, "system_drive_capacity": 494586032128, "platform": "windows", "os_version_and_architecture": "Windows 10 Pro 21H2 (64 bits)", "number_of_days_since_last_boot": 28, "number_of_days_since_last_logon": 0, "number_of_monitors": 1, "cpu_model": "Intel Core i3-7100 CPU @ 3.90GHz", "device_type": "desktop", "distinguished_name": "/DC=org/DC=tpmed/DC=si/OU=VDTOULON/OU=postes/CN=PCW-TOU-74141", "entity": "Noral", "last_system_boot": "2023-02-20T09:55:07", "last_boot_duration": 17795, "last_ip_address": "10.150.115.2", "last_logon_duration": 20000, "last_logon_time": "2023-02-20T10:07:31", "mac_addresses": ["50:9A:4C:48:DE:3B"]}}
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
-> For index="nexthink" sourcetype="st_nexthink_device"
{"date": 1676910383.7157812, "asset": {"name": "PCW-TOU-74141", "score:Device performance/Boot speed": 0.0, "total_ram": 8589934592, "total_nonsystem_drive_usage": null, "total_nonsystem_drive_capacity": 0, "system_drive_usage": 0.26, "system_drive_capacity": 494586032128, "platform": "windows", "os_version_and_architecture": "Windows 10 Pro 21H2 (64 bits)", "number_of_days_since_last_boot": 28, "number_of_days_since_last_logon": 0, "number_of_monitors": 1, "cpu_model": "Intel Core i3-7100 CPU @ 3.90GHz", "device_type": "desktop", "distinguished_name": "/DC=org/DC=tpmed/DC=si/OU=VDTOULON/OU=postes/CN=PCW-TOU-74141", "entity": "Noral", "last_system_boot": "2023-02-20T09:55:07", "last_boot_duration": 17795, "last_ip_address": "10.150.115.2", "last_logon_duration": 20000, "last_logon_time": "2023-02-20T10:07:31", "mac_addresses": ["50:9A:4C:48:DE:3B"]}}
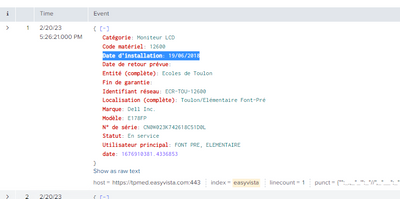
-> For index=easyvista sourcetype=st_easyvista_generic
{"date": 1676911288.1942825, "Date de r\u00e9solution": "20/02/2023 10:58:27", "D\u00e9lai de r\u00e9solution (hh:mm)": " 0:35", "D\u00e9lai de r\u00e9solution (min)": "35", "Enregistr\u00e9 le": "20/02/2023 10:23:39", "Entit\u00e9 (compl\u00e8te)": "Toulon/Direction Generale des Services/Direction Police Municipale", "Groupe responsable": "Centre de service", "N\u00b0 de demande": "S230220_007", "Origine de la demande": "Self Service", "Priorit\u00e9": "2", "Statut de la demande": "Cl\u00f4tur\u00e9"}
The field annee : is an extract from this field corresponding to the year of the date , so, annee for this example : annee=2018
It refers to this part of the previous query :
| rename "Identifiant réseau" as PC "Date d'installation" as dd | eval annee=mvindex(split(dd,"/"),-1) | eval date=strftime(now(),"%d/%m/%Y")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your second events don't appear to have fields "Identifiant réseau" or "Date d'installation". Having said that, are you trying to "join" events from the first search with event from the second search by PC?
index="nexthink" sourcetype="st_nexthink_device"
| spath "asset.last_boot_duration" output=boot | spath "asset.last_logon_duration" output=logon | spath "asset.name" output=PC | eval demarrage=boot+logon |eval date=strftime(now(),"%d/%m/%Y") |eval annee_now=mvindex(split(date,"/"),-1) | fields demarrage, PC
| append
[ |search index=easyvista sourcetype=st_easyvista_generic "Identifiant réseau"="PCW-*" Catégorie="Borne tactile" OR Catégorie="All in One" OR Catégorie="Convertible" OR Catégorie="Odinateurs de bureau" OR Catégorie="Ordinateurs portables" OR Catégorie="Ordinateurs format micro" OR Catégorie="Workstation"
| rename "Identifiant réseau" as PC "Date d'installation" as dd | eval annee=mvindex(split(dd,"/"),-1) | eval date=strftime(now(),"%d/%m/%Y") | eval annee_now=mvindex(split(date,"/"),-1) | eval difference=annee_now-annee |fields difference, PC ] | stats values(difference) as difference values(demarrage) as demarrage by PC