Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to coalesce events with different values for s...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to coalesce events with different values for status field?
x213217
Explorer
04-15-2019
08:05 AM
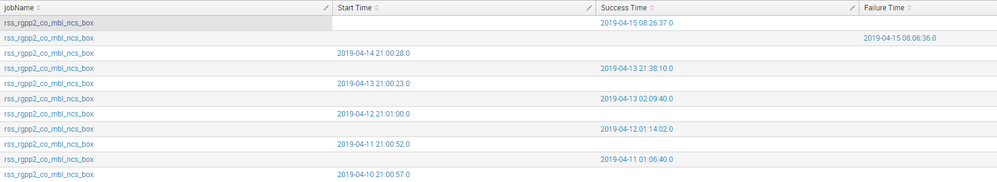
I have this search that will display the following
index=autosys source= jobName=
| where statusText="SUCCESS" OR statusText="RUNNING" OR statusText="FAILURE" OR statusText="JOBFAILURE"
| eval startTime=if(statusText=="RUNNING",timestamp,null)
| eval failureTime=if(statusText=="FAILURE",timestamp,null)
| eval successTime=if(statusText=="SUCCESS",timestamp,null)
| streamstats last(successTime) as prev_successtime,last(failureTime) as prev_failuretime,last(startTime) as prev_startTime current=f window=1
| table jobName startTime successTime failureTime
| rename startTime as "Start Time" successTime as "Success Time" failureTime as "Failure Time"
I would like to have the most recent startTime match up with the latest SuccessTime or FailureTime in the same row. Is this possible?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
woodcock
Esteemed Legend
04-15-2019
12:14 PM
Just add this to the end:
| selfjoin jobName
You can also do this:
| stats values(*) AS * BY jobName
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
grittonc
Contributor
04-15-2019
10:16 AM
Does this job only run once per day?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
x213217
Explorer
04-15-2019
10:33 AM
this one in particular yes, but there will be ones that run on a variety of schedules
Get Updates on the Splunk Community!
[Puzzles] Solve, Learn, Repeat: Dynamic formatting from XML events
This challenge was first posted on Slack #puzzles channelFor a previous puzzle, I needed a set of fixed-length ...
Enter the Agentic Era with Splunk AI Assistant for SPL 1.4
🚀 Your data just got a serious AI upgrade — are you ready?
Say hello to the Agentic Era with the ...
Stronger Security with Federated Search for S3, GCP SQL & Australian Threat ...
Splunk Lantern is a Splunk customer success center that provides advice from Splunk experts on valuable data ...