Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Search
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to build a Splunk search to build a table for ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
super_edition
Path Finder
05-30-2023
05:57 AM
Hello Everyone,
This is the extension of previous query which I posted- https://community.splunk.com/t5/Splunk-Search/How-would-I-write-a-Splunk-search-to-build-a-table-for...
Thanks to @ITWhisperer and updated query worked well.
Now I am trying to add percentage column for PASS and FAIL, instead of the count:
| _time | success | fail |
| 2023-05-28 03:00 | 98 | 2 |
| 2023-05-28 04:00 | 60 | 40 |
| 2023-05-28 05:00 | 100 | 0 |
I was trying to build a query, something like this:
index=my_index sourcetype=openshift_logs openshift_namespace=my_ns openshift_cluster="cluster009"
("message.statusCode"=2* OR "message.statusCode"=4*)
| eval status=if('message.statusCode'>300,"fail","success")
| search "message.logType"=CLIENT_RES
| search "message.url"="/shopping/carts/*"
```| timechart span=1h dc("message.tracers.ek-correlation-id{}") as count by status```
| eventstats count("message.tracers.ek-correlation-id{}") as totalCount
| eventstats count("message.tracers.ek-correlation-id{}") as individualCount by status
| eval percent=(individualCount/totalCount)*100
I know the above query is incomplete and not sure if this the right way to proceed.
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ITWhisperer

SplunkTrust
05-31-2023
12:22 AM
Just overwrite the success and fail fields
index=my_index sourcetype=openshift_logs openshift_namespace=my_ns openshift_cluster="cluster009"
("message.statusCode"=2* OR "message.statusCode"=4*)
| eval status=if('message.statusCode'>300,"fail","success")
| search "message.logType"=CLIENT_RES
| search "message.url"="/shopping/carts/*"
| timechart span=1h dc("message.tracers.correlation-id{}") as count by status pct
| addtotals
| eval success=round(100*success/Total,1)
| eval fail=round(100*fail/Total,1)- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ITWhisperer

SplunkTrust
05-30-2023
06:17 AM
Instead of the last 3 lines, try this
| addtotals
| eval successpercent=100*success/Total- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
super_edition
Path Finder
05-30-2023
10:29 PM
Hello @ITWhisperer
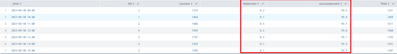
I am getting the below data as the result:
index=my_index sourcetype=openshift_logs openshift_namespace=my_ns openshift_cluster="cluster009"
("message.statusCode"=2* OR "message.statusCode"=4*)
| eval status=if('message.statusCode'>300,"fail","success")
| search "message.logType"=CLIENT_RES
| search "message.url"="/shopping/carts/*"
| timechart span=1h dc("message.tracers.correlation-id{}") as count by status pct
| addtotals
| eval successpercent=round(100*success/Total,1)
| eval failpercent=round(100*fail/Total,1)But I am looking for only successpercent and failpercent to be displayed in the table.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ITWhisperer

SplunkTrust
05-31-2023
12:22 AM
Just overwrite the success and fail fields
index=my_index sourcetype=openshift_logs openshift_namespace=my_ns openshift_cluster="cluster009"
("message.statusCode"=2* OR "message.statusCode"=4*)
| eval status=if('message.statusCode'>300,"fail","success")
| search "message.logType"=CLIENT_RES
| search "message.url"="/shopping/carts/*"
| timechart span=1h dc("message.tracers.correlation-id{}") as count by status pct
| addtotals
| eval success=round(100*success/Total,1)
| eval fail=round(100*fail/Total,1)- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
super_edition
Path Finder
05-30-2023
10:33 PM
this command helped:
|fields _time successpercent failpercent
Get Updates on the Splunk Community!
More Ways To Control Your Costs With Archived Metrics | Register for Tech Talk
Tuesday, May 14, 2024 | 11AM PT / 2PM ET
Register to Attend
Join us for this Tech Talk and learn how to ...
.conf24 | Personalize your .conf experience with Learning Paths!
Personalize your .conf24 Experience
Learning paths allow you to level up your skill sets and dive deeper ...
Threat Hunting Unlocked: How to Uplevel Your Threat Hunting With the PEAK Framework ...
WATCH NOWAs AI starts tackling low level alerts, it's more critical than ever to uplevel your threat hunting ...