Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to add values to the fields?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to add values to the fields?
ramesh12345
Explorer
03-05-2019
02:26 AM
Hi,
index="osh" sourcetype="Service" CaseNumber=1111 status=* assignment_group=*
| dedup _time,CaseNumber,assignment_group
| streamstats current=f last(assignment_group) as lg, last(active) as Active by CaseNumber
| lookup Team.csv SO as sys_updated_by OUTPUT TeamName
| eval is_escalated= if(assignment_group!=lg AND assignment_group="OSM L1",1,NULL)
| eval is_resolved=if(assignment_group="OSM L1" AND status="Complete" AND (isnull(Active) OR Active="true"),1,NULL)
| stats count(is_escalated) AS "Escalated Cases" count(is_resolved) AS "Resolved Cases" by sys_updated_by,TeamName
| fields - TeamName
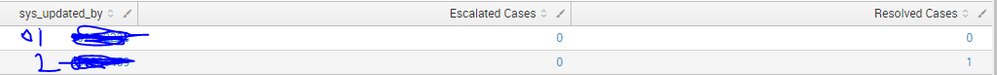
when i run this query it is displaying like that(attached image).
For that case number(1111) 2 members worked.so this case resolved case so the output should be 1 for two members.
if it is escalated cases then in escalated cases i should should assign 1.
How to do this?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
rsathish47
Contributor
03-05-2019
02:40 AM
Hi ,
you can use streamstats command for this
index=_internal | stats count by sourcetype | head 2| streamstats current=f last(count) as newcount
Thanks
Sathish R
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ramesh12345
Explorer
03-05-2019
03:08 AM
Could you please send me the final query.i am little bit confused.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
nickhills
Ultra Champion
03-05-2019
02:35 AM
You should post your searches using the code tool (icon which looks like 101010 ) I think some of the characters of your search have been stripped. - I edited this for you.
If my comment helps, please give it a thumbs up!
Related Topics
Get Updates on the Splunk Community!
Observe and Secure All Apps with Splunk
Join Us for Our Next Tech Talk: Observe and Secure All Apps with SplunkAs organizations continue to innovate ...
Splunk Decoded: Business Transactions vs Business IQ
It’s the morning of Black Friday, and your e-commerce site is handling 10x normal traffic. Orders are flowing, ...
Fastest way to demo Observability
I’ve been having a lot of fun learning about Kubernetes and Observability. I set myself an interesting ...