Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to add the average of the top 5 percent of val...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to add the average of the top 5 percent of values, but remove the max value, to my timechart?
What I have:
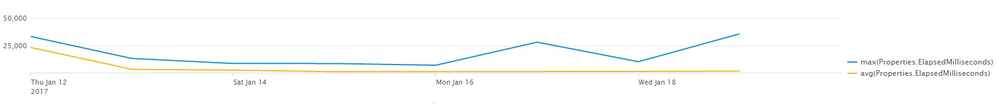
"Properties.MetricType"=ResponseTiming AND "Properties.Http_Request_Path"=/BackflushInputs | timechart max("Properties.ElapsedMilliseconds") avg("Properties.ElapsedMilliseconds")
This gives me a very nice graph:
Because the Max value can be a significant outlier from than the rest, I'd also like to display the average of the top 5% values, minus the max value.
I've found answers to somewhat similar questions here:
https://answers.splunk.com/answers/75965/top-percentage-out-of-total-events.html
https://answers.splunk.com/answers/61711/average-time-on-only-top-results.html
...but I'm having trouble morphing them to exactly what I want. Any ideas on how I can achieve this, adding it to my current chart? Thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
something like:
your query to return events
| eventstats perc95(Properties.ElapsedMilliseconds) as interestedValue
| search Properties.ElapsedMilliseconds < interestedValue
| stats avg(Properties.ElapsedMilliseconds) as Avg
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You may want to explore function percX aggregation function available in timechart (and stats/chart). This gives the X percentile value, so if you use perc95("Properties.ElapsedMilliseconds") in your timechart, it should skip the top 5% outliers.