Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How do you show events on a timeline?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How do you show events on a timeline?
Assuming I'm showing events on a timeline, say for example, timechart count(sign_ins) by date_hour
date_hour | user sign ins
10 | 120
11 | 151
12 | 122
13 | 100
14 | 532
15 | 332
And then I wish to show some markers on that timeline, e.g. stats first (promo_email) by date_hour
date_hour | email sent
10 | 'bacn'
13 | 'free stuff'
How could I represent the relationship between these two concepts in the same chart/report/dashboard?
Edit:
The relationship between them being that an event in the second search could cause a spike in the first search but splunk does not seem to have a way to draw lines/markers to show these.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi chustar,
you can combine both searches and simply use:
your base search here | timechart count(sign_ins) AS sign_ins first(promo_email) AS promo_email by date_hour
But be aware that you should not use the date_* fields; see this answer to learn more on that https://answers.splunk.com/answers/387130/why-is-date-hour-inconsistent-with-h.html
Hope this helps ...
cheers, MuS
Update:
The problem is that you want to show numbers and strings on a timechart, therefore this is tricky. But there is an eval trick where you can use values and make them field names 😉
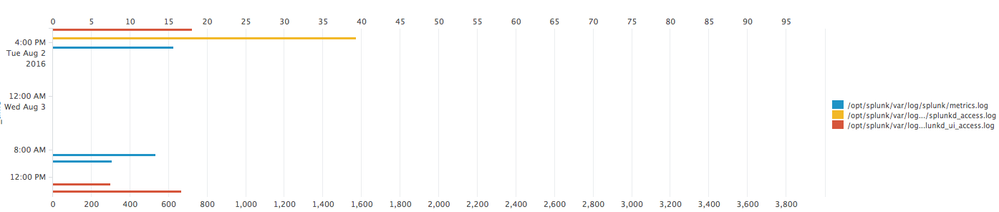
Take a look at this run everywhere command which will count kbps and use the first source of each hour as the filed name:
index=_internal source=*
| bin _time span=1h | streamstats first(source) AS first_source_by_hour by _time
| fields first_source_by_hour kbps
| eval {first_source_by_hour}=kbps
| timechart span=1h sum(*) AS * | fields - kbps
The result in a bar chart will look like this:
So, you could use your email promo instead of source and show it this way.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks MuS. This is what I'm doing now. I can keep it as a table, but I was hoping there was someway I don't know of to show it in a single chart (vertical line when the email is sent), or to call out that potential relationship somewhat better.
And thanks for the date_* tip.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
little update ping with a new idea