- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How do I modify my search so that it will show eit...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Howdy.
So I have two searches, which I have been asked to turn into "easy visualizations" so non-techies can look at it and go "This is bad, open a ticket."
Simple
index=location |search LockedStatus=Locked |rename UserAccountEntry as User |stats count as total by Location | sort 10 -total
Detailed
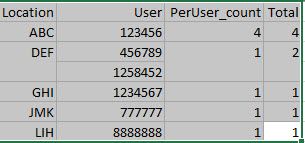
index=location |search LockedStatus=Locked |rename UserAccountEntry as User |stats count by Location User | stats list(User) as User list(count) as PerUser_count sum(count) as Total by Location | sort 10 -Total
(example of output of the details attached)
Just using the Visualization tab does not give me anything on a Marker Gauge, while the Single Value shows the location with the highest count. My understanding is they want to show the total number of today's account locks on the Marker Gauge and on the Single Value show today and show if its higher or lower then yesterday and by how much.
Having not used these before, looking for guidance.
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For the Marker Gauge, try this (repeat for each location, since marker gauge can only show one number)
index=location LockedStatus=Locked Location=* earliest=@d | stats count as total
For Single Value, try this (again, repeat for each location, if neeed)
index=location LockedStatus=Locked Location=* earliest=-1d@d | timechart count span=1d
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For the Marker Gauge, try this (repeat for each location, since marker gauge can only show one number)
index=location LockedStatus=Locked Location=* earliest=@d | stats count as total
For Single Value, try this (again, repeat for each location, if neeed)
index=location LockedStatus=Locked Location=* earliest=-1d@d | timechart count span=1d
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you, I will try that.
Is there a way I could sum the total and use that as my number?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sum which total? For single value comparison (show today and show if its higher or lower then yesterday and by how much) you will need both values. For Marker, there is only one number (total).
If you are referring to summing the total in your original query, you will have to end up with a single row for the gauge. It cannot accept multiple values. So you end result will have only the totals row.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Figured out how to change my query for the Marker. Your comment got me thinking. Thank you.
For the single value, the comparison of yesterday to today seems to be where I am missing something.
This is the search I am using, granted it gives me everything, not just the top 10, but I can live with that.
index=location |search LockedStatus=Locked |rename UserAccountEntry as User |stats count as total
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For single value with comparison, you will need two values. Current and Previous. The panel, automatically picks the value from the second row for Previous and shows the comparison. You current search only returns one value. Also, in your search, it would be more efficient to move the LockedStatus=Locked to the first segment and since you're not using the user field, you can skip the rename.