Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How do I get a subtraction of two fields when they...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
pal_sumit1
Path Finder
10-13-2018
08:55 AM
I am having three columns in primary_key, service_name , timestamp.
I want to get a subtraction of values present in the timestamp where their corresponding service_name is same.
And, if we are having more that 2 same fields, then we should get the average of both of the results.
Sample Data :
primary_key ------service_name------timestamp
123 "before abc" " 2-2-2018"
123 "after "abc" "2-3-2018"
123 "before abc" " 2-4-2018"
123 "after abc" "2-5-2018"
Desired result :
value=(("2-3-2018" - "2-2-2018")+("2-5-2018"-"2-4-2018" ))/2
Thanks in Advance
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
renjith_nair
Legend
10-13-2018
08:52 PM
@pal_sumit1,
Try
"your current search"|eval _time=strptime(timestamp,"%d-%m-%Y")
|sort primary_key,_time
|streamstats last(_time) as prev_time current=f window=1 by primary_key
|eval diff=_time-prev_time
|streamstats count as rowno by primary_key reset_on_change=true
|eventstats avg(eval(if(rowno%2==0,diff,null()))) as average by primary_key
|table primary_key,service_name,timestamp,diff,average
- You shall replace
eventstatswithstatsif you just want the final result with primary_key and avg difference - Ignored events if there is only one event - for eg only "before" event and not an "after" event
- Average is displayed in all events for that particular primary key
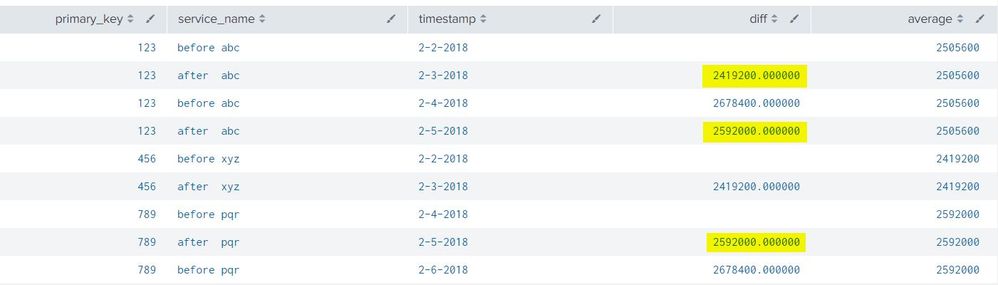
Sample data used :
primary_key,service_name,timestamp
123,"before abc",2-2-2018
123,"after abc",2-3-2018
123,"before abc",2-4-2018
123,"after abc",2-5-2018
456,"before xyz",2-2-2018
456,"after xyz",2-3-2018
789,"before pqr",2-4-2018
789,"after pqr",2-5-2018
789,"before pqr",2-6-2018 --> this event is ignored for the calculation since there is no pair for it.
Lets know if you need any modification.
Only those highlighted values are considered for avg calculation
---
What goes around comes around. If it helps, hit it with Karma 🙂
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
renjith_nair
Legend
10-13-2018
08:52 PM
@pal_sumit1,
Try
"your current search"|eval _time=strptime(timestamp,"%d-%m-%Y")
|sort primary_key,_time
|streamstats last(_time) as prev_time current=f window=1 by primary_key
|eval diff=_time-prev_time
|streamstats count as rowno by primary_key reset_on_change=true
|eventstats avg(eval(if(rowno%2==0,diff,null()))) as average by primary_key
|table primary_key,service_name,timestamp,diff,average
- You shall replace
eventstatswithstatsif you just want the final result with primary_key and avg difference - Ignored events if there is only one event - for eg only "before" event and not an "after" event
- Average is displayed in all events for that particular primary key
Sample data used :
primary_key,service_name,timestamp
123,"before abc",2-2-2018
123,"after abc",2-3-2018
123,"before abc",2-4-2018
123,"after abc",2-5-2018
456,"before xyz",2-2-2018
456,"after xyz",2-3-2018
789,"before pqr",2-4-2018
789,"after pqr",2-5-2018
789,"before pqr",2-6-2018 --> this event is ignored for the calculation since there is no pair for it.
Lets know if you need any modification.
Only those highlighted values are considered for avg calculation
---
What goes around comes around. If it helps, hit it with Karma 🙂
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
renjith_nair
Legend
10-26-2018
04:41 AM
@pal_sumit1, did it work for you ? If yes, accept it as answer or lets know whats missing.
---
What goes around comes around. If it helps, hit it with Karma 🙂
What goes around comes around. If it helps, hit it with Karma 🙂
Career Survey
First 500 qualified respondents will receive a $20 gift card! Tell us about your professional Splunk journey.
Get Updates on the Splunk Community!
Data Persistence in the OpenTelemetry Collector
This blog post is part of an ongoing series on OpenTelemetry.
What happens if the OpenTelemetry collector ...
Introducing Splunk 10.0: Smarter, Faster, and More Powerful Than Ever
Now On Demand
Whether you're managing complex deployments or looking to future-proof your data ...
Community Content Calendar, September edition
Welcome to another insightful post from our Community Content Calendar! We're thrilled to continue bringing ...