- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How do I add a CSV file as an input to show the he...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
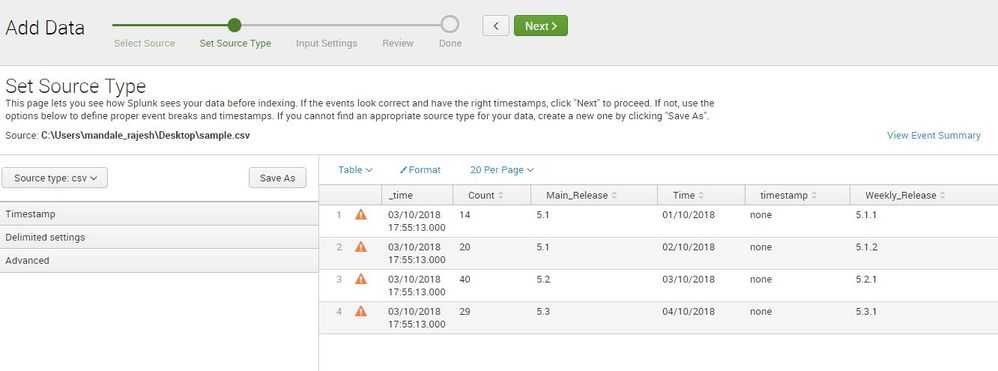
I am trying to add the below CSV file data into Splunk as an input through the ‘Add Data’ section.
Time, Main_Release, Weekly_Release, Count
01/10/2018, 5.1, 5.1.1, 14
02/10/2018, 5.1, 5.1.2, 20
03/10/2018, 5.2, 5.2.1, 40
04/10/2018, 5.3, 5.3.1, 29
After adding the data, the events which are showing under my index and source type are as follows
Event-1 -> 01/10/2018, 5.1, 5.1.1, 14
Event-2 ->02/10/2018, 5.1, 5.1.2, 20
Event-3 ->03/10/2018, 5.2, 5.2.1, 40
Event-4 ->04/10/2018, 5.3, 5.3.1, 29
But what I am expecting is
Event-1 -> Time=01/10/2018, Main_Release=5.1, Weekly_Release=5.1.1, Count=14
Event-2 -> Time=02/10/2018, Main_Release=5.1, Weekly_Release=5.1.2, Count=20
etc.,
I am expecting the header of the CSV file to be the respective fields for each values. But it is giving me only the values available in the CSV file cell.
Could anyone please help me on this to achieve header as the field name for each events with field values?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you try with query-
index=<indexname>|table Time, Main_Release, Weekly_Release, Count
it should give you expected output.
you can see below events are extracted with column header as expected.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you try with query-
index=<indexname>|table Time, Main_Release, Weekly_Release, Count
it should give you expected output.
you can see below events are extracted with column header as expected.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @493669 ,
Thanks for your response. In the above method which you mentioned I am able to display my data on dashboard panels.
But just want to know, is there any other way to index the values with their field names in each events while adding the input file itself.
Instead of showing the below:
Event-1 -> 01/10/2018, 5.1, 5.1.1, 14
Event-2 ->02/10/2018, 5.1, 5.1.2, 20
Can we get in this way:
Event-1 -> Time=01/10/2018, Main_Release=5.1, Weekly_Release=5.1.1, Count=14
Event-2 -> Time=02/10/2018, Main_Release=5.1, Weekly_Release=5.1.2, Count=20
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't think Splunk will give in such manner but in similar way you can get in table fashion because in events splunk will show as raw i.e. the events present in csv in same way splunk will show
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay got it. Thankyou