Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How can I fix tstats error after upgrading to Splu...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
we had successfully upgraded to Splunk 9.0.4. However, we observed that when using tstats command, we are getting the below message. normal searches are all giving results as expected.
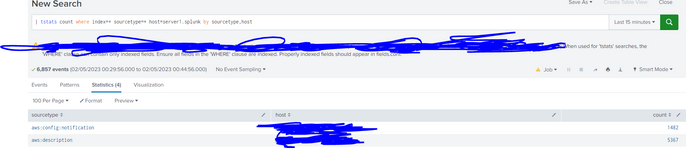
[indexer1,indexer2,indexer3,indexer4.indexer5] When used for 'tstats' searches, the 'WHERE' clause can contain only indexed fields. Ensure all fields in the 'WHERE' clause are indexed. Properly indexed fields should appear in fields.conf.
Any idea why we are getting this and how to resolve it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @keishsplunk,
I don't know if something changed in the Splunk last version, but you should try to move the fields in the WHERE condition after the tstats command when they are also the BY fields, something like this:
| tstats count WHERE index=* BY sourcetype host
| search host=your_hostor
| tstats count WHERE index=* host=your_host BY sourcetypeCiao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are experiencing the same issue after Upgrading from 8.2.9 to 9.0.5. Any Updates / Infos available?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Change the SPL syntax as such -
| tstats count where index=* by sourcetype,host | search sourcetype=* host=heavy-forwarder-1
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @keishsplunk ,
good for you, see next time!
Ciao and happy splunking
Giuseppe
P.S.: Karma Points are appreciated 😉
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @keishsplunk,
I don't know if something changed in the Splunk last version, but you should try to move the fields in the WHERE condition after the tstats command when they are also the BY fields, something like this:
| tstats count WHERE index=* BY sourcetype host
| search host=your_hostor
| tstats count WHERE index=* host=your_host BY sourcetypeCiao.
Giuseppe