Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Help in using CASE Statement
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Noob_splunker
Explorer
07-04-2020
01:57 PM
Hi there,
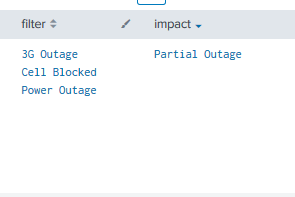
I want to group the filter into Full Outage or Partial Outage.
| filter | impact |
3G Outage | Full Outage |
Cell Blocked | |
Power Outage | |
| Power Outage | Partial Outage |
Cell Blocked |
Here is my query:
| eval impact=case(
searchmatch("Cell Blocked"),"Partial Outage",
searchmatch("3G Outage"),"Full Outage",1=1,"No service impact")
Result:
The correct impact should be Full Outage. Can anyone help me out?
Thanks,
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
to4kawa
Ultra Champion
07-04-2020
03:42 PM
| makeresults
| eval filter=split("3G Outage,Cell Blocked,Power Outage",",")
| rename COMMENT as "this is sample"
| rename COMMENT as "the logic"
| eval impact=case(match(filter,"3G Outage"),"Full Outage",match(filter,"Cell Blocked"),"Partial Outage",1=1,"No service impact")
filter is multivalue ,searchmatch() works only _raw and case() works in order.
How about this?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
to4kawa
Ultra Champion
07-04-2020
03:42 PM
| makeresults
| eval filter=split("3G Outage,Cell Blocked,Power Outage",",")
| rename COMMENT as "this is sample"
| rename COMMENT as "the logic"
| eval impact=case(match(filter,"3G Outage"),"Full Outage",match(filter,"Cell Blocked"),"Partial Outage",1=1,"No service impact")
filter is multivalue ,searchmatch() works only _raw and case() works in order.
How about this?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Noob_splunker
Explorer
07-04-2020
03:57 PM
Get Updates on the Splunk Community!
Index This | What is broken 80% of the time by February?
December 2025 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with this ...
Unlock Faster Time-to-Value on Edge and Ingest Processor with New SPL2 Pipeline ...
Hello Splunk Community,
We're thrilled to share an exciting update that will help you manage your data more ...
Splunk MCP & Agentic AI: Machine Data Without Limits
Discover how the Splunk Model Context Protocol (MCP) Server can revolutionize the way your organization uses ...