Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- File Comparision
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
File Comparision
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a file, say abc.csv, which I indexed once having events a b c , then i indexed it again after some days updating it, having events a b c d, again i indexed it at some point of time, having events a c and again then i uploaded it having events a b c.
My desired output
date 2- d
date 3- c
date 4- same
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can you add more details?
this file is already indexed? where are stored the file? maybe it's better a versioning software?
Regards
Alessandro
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a file, say abc.csv, which I indexed once having events a b c , then i indexed it again after some days updating it, having events a b c d, again i indexed it at some point of time, having events a c and again then i uploaded it having events a b c.
My desired output
date 2- d
date 3- c
date 4- same
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
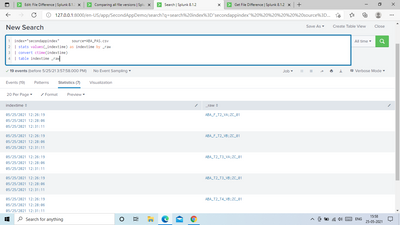
Try this search to check when is indexed an event
index=<your index>
| eventstats count by _raw
| where count=1
| table source _indextime _raw
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This solution only compares the last and latest ones.. can u give something which compares the latest to all the previous ones.
Regards
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
this search compares the previous event data to the last event data based on your timerange
|
stats min(_indextime) as min_indextime max(_indextime) as max_indextime | convert ctime(min_indextime) ctime(max_indextime)- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sir can u please elaborate the code , how to frame it properly
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
please describe how you would like the output search.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index= <your index>
| stats values(_indextime) as indextime by _raw | convert ctime(indextime)- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This solution gives _raw present in all the versions. Not the event which is different.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ok now you can expand your indextime field
index= <your index>
| stats values(_indextime) as indextime by _raw | convert ctime(indextime)
| mvexpand idextime
| table idextime _raw