- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Field-extraction wizard error: "The extraction fai...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just started indexing Windows printer logs and noticed I need to add some additional fields to extract. Here is an example of one of the events:
LogName=Microsoft-Windows-PrintService/Operational
SourceName=Microsoft-Windows-PrintService
EventCode=307
EventType=4
Type=Information
ComputerName=Server1
User=Bob
Sid=SIDHere
SidType=1
TaskCategory=Printing a document
OpCode=Spooler Operation Succeeded
RecordNumber=1234
Keywords=Document Print Job, Classic Spooler Event
Message=Document 123, Print Document owned by Bob on Workstation1 was printed on Printer1 through port IP_127.0.0.1. Size in bytes: 123456. Pages printed: 1. No user action is required.
What I want to do is add fields with these name that put out these variables from the Message field:
DocumentOwner=Bob,
PrinterClient=Workstation1,
Printer=Printer1,
PrinterPort=IP_127.0.0.1
When I go to the field extractor and use the wizard I am able to highlight and label the first two fields I want but when I highlight and add the third or fourth field I get the error:
"The extraction failed. If you are extracting multiple fields, try removing one or more fields. Start with extractions that are embedded within longer text strings."
I tried breaking it up and just add two fields at a time but when I add two fields and save then go back in and do a new extraction and try to highlight and add an additional field I get the same error message. Looks like I do not understand what the meaning of the error is.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try exatracting fields seperately...as you are refering only one event for all the fields which may be different than any other event. Or manually edit the regular expression if you want everything in one regex
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The field extractor, when successful, adds that new field to Splunk settings, rather than just this one search. Meaning, only one is allowed at a time.
If you want to extract fields just from one search, rather than changing all of your Splunk searches, you'll be needing to extract it in the search string itself. This involves the rex command, and learning some regular expression programing.
So it might involve something like:
| rex (Document\sowned\sby\s)(?<owner>[\w?\d?]+)\s
to get the field for the owner. A fun way to learn more about regex is at this site: https://regexone.com
Or, if you don't care to learn regular expressions, you can take the Field Extractor to the point where it has figured out the extraction, and just copy it out of the "Show regex" area, and not save the extraction.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks I agree, that was going to be my backup plan if I could not get splunk to pull it out through it's regex wizard. Just wanted to avoid having to relearn it then forget it again five minutes later at all costs. Usually takes me about an hour and a few dents in my desk and head to rewrap my head around it then once the task is complete poof it's gone again haha.
Thank you for providing a basic example at that was exactly what I was looking for to make the first field.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are welcome, I'm still learning regex myself so I am glad I was able to help at least a bit.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am posting a second answer, because this does not really address your question about IFX, however...
In your inputs, where you specify the WinEventLog stanza for your printerlogs, if you set renderXML=1 the forwarder will collect these logs as XML. You can then configure XML KV extractions in your props file, and it will do all the extractions for you, or you can use spath to extract the fields in your search.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That is interesting I initially tried the renderXML switch in the stanza as I saw it on another post about pulling out the printer logs just to see what it looked like. Lo and behold it did exactly like it said it would and it was formatted in XML.
Since I am a run of the mill Ops guy I saw that and said no no no give me back something I am used too and is more human readable. So I changed it back without really looking at it. If it does a better job of dealing with field extraction or at least a cleaner way of doing it I may have to turn it back on and play with what you suggested. If anything so I know what it is capable of doing going forward for future situations like this.
Thank you for sugesting it!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
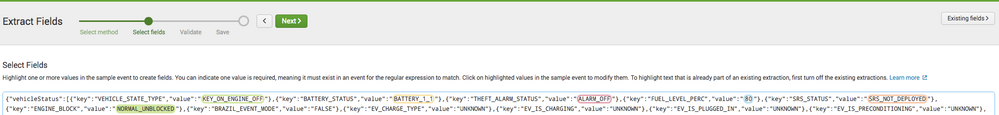
This happens when the field extractor can't form a concise enough extraction to capture all the data you want.
Ideally - you write your own regex at this point because you can probably do a better job that IFX for long/complex extractions.
However - I have found that sometimes the IFX struggels if it is "showing" the previous extractions whilst you are performing more.
A workaround is to do the following:
1.) when you see that error - remove the last field you just added (click it and remove) Then save your extractions.
2.) click extract more fields, you will now see your previous extractions outlined in the IFX.
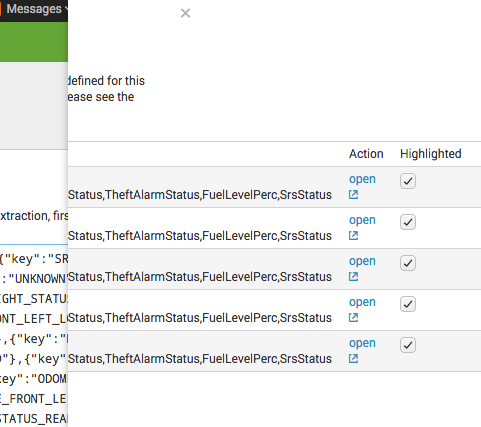
3.) Click "Existing Fields"
4.) From the pop-out menu select some/all of your previous extractions and untick 'highlighted' which will remove the outlining, continue to perform extraction, until you see the error again, or you are finished.
5.) Rinse/repeat
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think I tried exactly what you recommended before I just ended up breaking up each new field into it's own extraction but ran into the same issue. When I tried putting in two the the fields into a single extraction then went back and tried to create a new extraction one one of the two remaining fields I needed I got the error.
Then I tried as you suggested and un-checked the highlighted fields I was already extracting and still got the error after re-attempting to create the new field. I am sure did something in the wrong order and this would have worked but it was a dead end when I attempted it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try exatracting fields seperately...as you are refering only one event for all the fields which may be different than any other event. Or manually edit the regular expression if you want everything in one regex
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This was the quick fix to my issue, I just separated each extraction into it's own field extraction and I got it working enough to achieve the main goal. It's not the best solution but it worked in a pinch and kept me from needing to re-lean regex for the 100th time. (I have a super bad memory and am a bit lazy/in a hurry) 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey you are welcome
I have converted my comment to an answer
As you have already accepted an answer...you can upvote/accept my answer if you can !
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you myurr98, and thank you for your help!