Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Extracting using rex
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Extracting using rex
How do I use rex to extract the virus info so that I can display this info in my splunk dashboard?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
getting the end of line after VIRUS - try the next
index=<YOUR INDEX HERE> source="General-linux-sql.log" sourcetype="Linux" Virus
| rex "\s+VIRUS\s+-\s+(?<virusDescription>.*)"
| table _time virusDescription
r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I need to put the following line first as this is where i'll be retrieving my info from
So do i add your code after this line?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes add it to after those. You should always add at least
index=<your index> sourcetype=<your sourcetype> source=<your source> when you are looking events. And in this case add also word “Virus” as it would be on your each event.
That way your query is more powerful, quicker and use less resources.
I updated my previous example to contain these.
r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Do you want to get that "Virus" word in a separate field using rex command
or do you want to show the log details in the dashboard which has a virus word?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@impurush Hi. I just want to get "Possible NewApt.Worm - gadget.exe", "Possible Y2K Zelu Trojan", and "Possible NewApt.Worm - baby.exe"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @rkris , use the below query to get all three "Possible NewApt.Worm - gadget.exe", "Possible Y2K Zelu Trojan", and "Possible NewApt.Worm - baby.exe" from the logs.
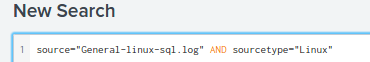
source="General-linux-sql.log" sourcetype="Linux" ("Possible NewApt.Worm - gadget.exe" OR "Possible Y2K Zelu Trojan" OR "Possible NewApt.Worm - baby.exe")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there a way for me to group them all into a table?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@rkris , you can try this
source="General-linux-sql.log" sourcetype="Linux" ("Possible NewApt.Worm - gadget.exe" OR "Possible Y2K Zelu Trojan" OR "Possible NewApt.Worm - baby.exe")
|rex field=_raw "Virus\s-\s(?<virus_name>.*)"
| table _time,virus_name