Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Extract count of each value of a field and create ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Extract count of each value of a field and create a timechart from it using stats
priyangshupal
Engager
10-29-2021
12:23 AM
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
tread_splunk

Splunk Employee
10-29-2021
04:34 AM
But if you really want to introduce the V1, V2, V3 field names you'll need...
index=_* index=_internal sourcetype=splunkd
| rename component as skill
| timechart span=5m count by skill limit=0
| untable _time skill count
| sort skill, _time
| streamstats dc(skill) as counter
| eval fieldnameReq="v".counter
| timechart span=5m sum(count) by fieldnameReq limit=0
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
tread_splunk

Splunk Employee
10-29-2021
04:32 AM
I think this is what you mean. The hardest part is introducing the v1,v2,v3 etc field names.
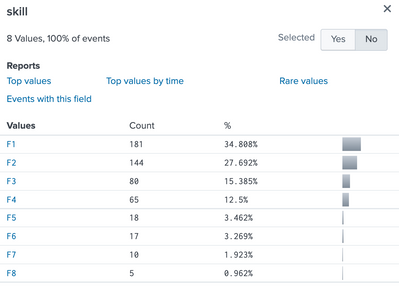
If you're happy to retain the skill values, i.e. F1, F2, F3 (in your screenshot above) as the field names, then this becomes much simpler i.e....
index=_* index=_internal sourcetype=splunkd
| rename component as skill
| timechart span=5m count by skill limit=0 - Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
tread_splunk

Splunk Employee
10-29-2021
04:18 AM
Something like this...
index=_* index=_internal sourcetype=splunkd
| rename component as skill
| stats count by skill
| streamstats count as counter
| eval fieldnameReq="v".counter,stub="sum"
| chart sum(count) over stub by fieldnameReq limit=0
| fields - stubReplace first 2 lines with your query. Working on another post that produces a timechart. 2 tics
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
tread_splunk

Splunk Employee
10-29-2021
04:51 AM
Neater solution, using transpose command.
index=_* index=_internal sourcetype=splunkd
| rename component as skill
| stats count by skill
| streamstats count as counter
| eval fieldnameReq="v".counter
| fields - counter skill
| transpose header_field=fieldnameReqCareer Survey
First 500 qualified respondents will receive a $20 gift card! Tell us about your professional Splunk journey.
Get Updates on the Splunk Community!
.conf25 Global Broadcast: Don’t Miss a Moment
Hello Splunkers,
.conf25 is only a click away.
Not able to make it to .conf25 in person? No worries, you can ...
Observe and Secure All Apps with Splunk
Join Us for Our Next Tech Talk: Observe and Secure All Apps with SplunkAs organizations continue to innovate ...
What's New in Splunk Observability - August 2025
What's New We are excited to announce the latest enhancements to Splunk Observability Cloud as well as what is ...