- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Creating report search issues
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
I am trying to create an efficient way to pull out certain win events for my report but I am not sure it would return the results I want. It truncates some of the results. I might be doing something wrong. Please see the code that I am currently running and suggest an improvement. Thank you all!
index=mbda_windows_server sourcetype=XmlWinEventLog EventCode=4718 OR 4728 OR 4729 OR 4730 OR 4732 OR 4733 OR 4756 OR 4757 OR 4762 OR 4796 OR 5136
| dedup src_user, MemberSid, Group_Domain, Group_Name, host, _time
| convert timeformat="%d/%m/%Y %H:%M" ctime(_time)
| rename src_user AS Login, MemberSid AS Account, Group_Domain AS Domain, Group_Name AS Group, host AS Host, _time AS Min_NormDateMin, name AS EventName
| table Login, Account, Domain, Group, Host, Min_NormDateMin, EventCode, EventName | sort EventCode
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If I understand correctly you want to remove duplicates based on a field with different names across certain events. If so simply create a field that is common across them with coalesce, as in:
| eval myfield = coalesce(fieldname1, fieldname2, fieldname3, ...)
Then use dedup based on myfield.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also, I wanted to know what would be the best way to automatically email the report results to me scheduled every day at 10 AM?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
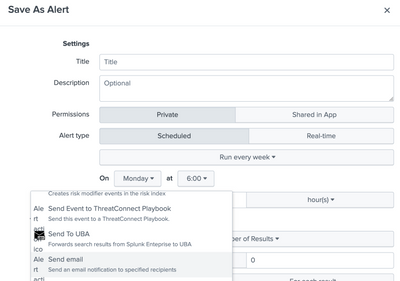
Run the search, then click on "Save As" > Alert and chose your schedule and within "Trigger Actions" select "Send email".

- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did that yesterday, but no report laded into my email box. Do I need to configure something else?
Thank you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have to configure the email notification settings:
https://docs.splunk.com/Documentation/Splunk/9.0.0/Alert/Emailnotification
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you @javiergn
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How can I remove the duplicates efficiently as not all events contain the same fields and these events will be dropped? I need to remove the duplicates anyway.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, the first line is wrong, try using one of the following two:
index=mbda_windows_server sourcetype=XmlWinEventLog EventCode IN (4718, 4728, 4729, 4730, 4732, 4733, 4756, 4757, 4762, 4796, 5136)
index=mbda_windows_server sourcetype=XmlWinEventLog (EventCode=4718 OR EventCode=4728 OR EventCode=4729 OR EventCode=4730 OR EventCode=4732 OR EventCode=4733 OR EventCode=4756 OR EventCode=4757 OR EventCode=4762 OR EventCode=4796 OR EventCode=5136)- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the swift reply. Please let me know how to remove duplicates that do not have the same fields. I would like to avoid dropping events because of this? Thank you!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If I understand correctly you want to remove duplicates based on a field with different names across certain events. If so simply create a field that is common across them with coalesce, as in:
| eval myfield = coalesce(fieldname1, fieldname2, fieldname3, ...)
Then use dedup based on myfield.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the help, @javiergn
Much appreciated!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sure no problem. Don't forget to mark the above as answered so that we can close the thread.
Regards,
Javier