Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Count the number of api occurrence in 10 second
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Count the number of api occurrence in 10 second
JyotiP
Path Finder
09-27-2019
01:40 AM
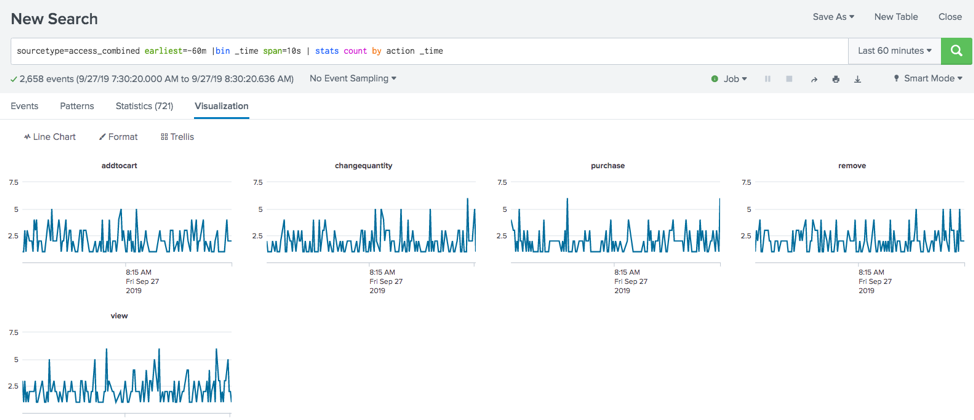
I have the following API's, for which I need to count the occurrence of each in every 10 seconds for 1 hour time interval.
/api/login/v1/session
/api/data/v1/graphql
/api/order/v1/orders
/api/order/v1/states
/api/order/orderimporter/v1/importcsv
/api/order/orderimporter/v1/promote
/api/order/orderimporter/v1/stagingOrder
/api/order/v3/graphql
/api/order/desk/v2/quickSend
/api/order/v1/desk/Batch/sync
/api/order/v1/Orders/sync
I tried with
host=*localhost* Path=*** sourcetype=nginx
| where Path in ("/api/platform/v1/session" OR "/api/coredata/v1/graphql" OR "/api/trading/v1/orders")
| table Path
But getting Error in 'where' command: Typechecking failed. 'OR' only takes boolean arguments
Basically I want the count of all the listed api in every 10 seconds for 1-hour interval.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
kmorris_splunk

Splunk Employee
09-27-2019
05:36 AM
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
techiesid

SplunkTrust
09-27-2019
01:46 AM
It should be smething like below,
host=*localhost* Path=*** sourcetype=nginx
| search Path IN ("/api/platform/v1/session" ,"/api/coredata/v1/graphql" , "/api/trading/v1/orders")
| table Path
| timechart count span=10s
Sid
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
JyotiP
Path Finder
09-27-2019
02:13 AM
@techiesid this work fine without timechart count span=10s, when I use this no result is coming
Get Updates on the Splunk Community!
[Puzzles] Solve, Learn, Repeat: Dynamic formatting from XML events
This challenge was first posted on Slack #puzzles channelFor a previous puzzle, I needed a set of fixed-length ...
Enter the Agentic Era with Splunk AI Assistant for SPL 1.4
🚀 Your data just got a serious AI upgrade — are you ready?
Say hello to the Agentic Era with the ...
Stronger Security with Federated Search for S3, GCP SQL & Australian Threat ...
Splunk Lantern is a Splunk customer success center that provides advice from Splunk experts on valuable data ...