Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Compare the login IP of the last time or previous ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Compare the login IP of the last time or previous 7 days to find the abnormal login
hello everyone. I have an alert requirement . an administort has login the device. I want to compare his current IP address with that of the last time or previous 7 days,If different, then alert. However, there are multiple administrator accounts, the fixed IP address used by each administrator may also be different. For example, admin often uses IP 2.2.2.2 to log in to the device, and admin2 often uses IP 3.3.3.3 to log in to the device
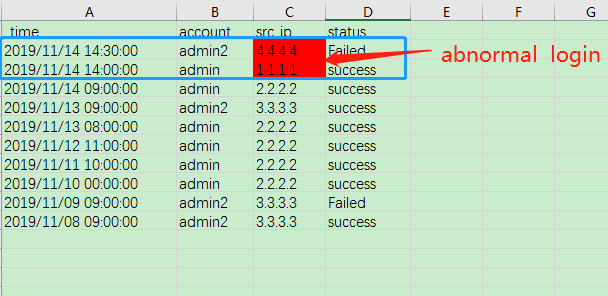
On November 14, 2019 . These two administrators use a different IP login device than usual. I think this is an abnormal behavior, whether they login successfully or fail
_time account src_ip status
2019/11/14 14:30:00 admin2 4.4.4.4 Failed
2019/11/14 14:00:00 admin 1.1.1.1 success
2019/11/14 09:00:00 admin 2.2.2.2 success
2019/11/13 09:00:00 admin2 3.3.3.3 success
2019/11/13 08:00:00 admin 2.2.2.2 success
2019/11/12 11:00:00 admin 2.2.2.2 success
2019/11/11 10:00:00 admin 2.2.2.2 success
2019/11/10 00:00:00 admin 2.2.2.2 success
2019/11/09 09:00:00 admin2 3.3.3.3 Failed
2019/11/08 09:00:00 admin2 3.3.3.3 success
How should I write this spl and configure alert?
I want to check the login log every 5 minutes, and then compare the login IP with that of the previous 7 days OR last time
all the help will be appreciated
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This approach is rather tricky. Especially because you're going to be running this alert's search every x minutes. It could be that the previous address was the attacker and the latest address was the normal login.
What might make more sense is to simply do something like:
...
| stats count by user,src
And then add some logic to find outliers (ie. user,src combinations that have significantly lower count than other combinations for that same user).
That, or use one saved search (that you run daily/weekly) to find the most common src for each user and write that to a lookup / summary index. And then use a second search to find any deviations from that.
Which solution works best also depends a bit on how frequently they log on and how dynamic their real IP address is.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does Splunk Enterprise Security have such anomaly detection function?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not with a simple single search command or so, no. The most basic way would be to just use that stats, look at the results and then think of some threshold (e.g. any counts ❤️ are suspicious). But you can also do some more elaborate statistics on it to calculate a threshold per user (maybe some admins are more dynamic in what IP they use than others).
Splunk's Machine Learning Toolkit could also be used, but that might be a bit overkill.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
you may also be two scenarios to consider:
account
adminmay not have been logged in before. Now the accountadminis logged in. If it is compared with the last time or previous 7 days, it will not find a historical data that can be referenced,this scenario needs to be alert.account
adminmay have 2 or more IP addresses in the previous 7 days, In this scenario, I only need to compare the IP address of the last login. If it is inconsistent,then alert