Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Avg disappears if I add min and max, so how do I c...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Avg disappears if I add min and max, so how do I combine avg, min, and max together to have all the stats I need?
I have events with response_time fields coming from an access log file. I have to display the average, min, and max response times sorted by another field called repository. My search looks like this:
<base_search>
| stats min(response_time) as min max(response_time) as max avg(response_time) as avg by repository
The average column is empty while I have min and max calculated correctly.
Now, if I remove min and max from my stats command average is calculated as expected.
The response_time field is numeric.
How do I combine avg, min, and max together to have all the stats that I need?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What happens if you just try min and avg or max and avg (i.e. not all 3)?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I should have mentioned that I already tried it too.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you change renamed values, try to use minimum instead of min, maximum instead of max, average instead of avg.
min, max and avg are function keywords may be that could be reason.
If this helps, give a like below.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My original stats command looked like this and it didn't work:
| stats min(response_time) as min_response_time, max(response_time) as max_response_time, avg(response_time) as avg_response_time by repositoryHowever I tested it once again, and confirmed that it doesn't help.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
if you get min and max, but avg is empty it usually means that your field is not numeric. Can you check it and convert to numeric if needed?
r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you mean something like this?
| eval resp_time=tonumber(response_time)
| stats min(resp_time) as minimum, max(resp_time) as maximum, avg(resp_time) as average by repositoryWith this search I don't have any results, not even the min and max values.
And don't forget that avg is only empty if I add min and max to the search. Without min and max I have average. I also examined the events and I can see this if I select the response_time field:
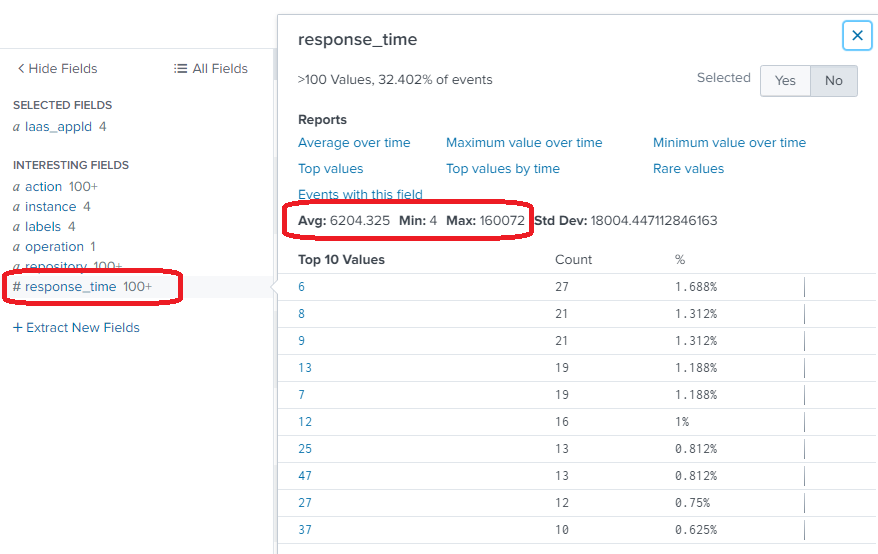
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
a -> String
# -> Number
That is the easiest way to check the type of field.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe it's time for support case to splunk?
btw. which version you are running and which OS?
r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's Splunk 8.0.1.
I don't know the OS but most likely our firm's RHEL 7 based internal Linux build
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you post the whole query as the issue is probably somewhere else than this stats?
And is the avg only function which is not working or is the same also e.g. for median, p90 etc.?
And no mater if you change the order of those?
Anything on job inspector?
r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is the whole query:
index="log-39337-prod-c" laas_appId="gitscm.stash*-bitbucket-access" status=200 username!=" - " labels!=" - "
| fields labels, response_time, action, laas_appId
| rex field=laas_appId "gitscm.(?<instance>(.*))-bitbucket-access"
| rex field=labels ".+(?<operation>refs|fetch|push|clone|archive)"
| search operation=clone
| rex field=action ".+\/scm\/(?<repository>.+)\.git.+"
| stats min(response_time) as minimum, max(response_time) as maximum, avg(response_time) as average by repository- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Probably next step is to create ticket to splunk support.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah, everyone seems to run out of ideas so I guess I don't have any other option.
Thank you for the help.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does putting commas between or using different names help?
<base_search>
| stats min(response_time) as minimum, max(response_time) as maximum, avg(response_time) as average by repository- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, that doesn't help. In fact, that was my initial version and I removed the commas because I saw examples without them here in the forum.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
