Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Aliasing and Graphing events at search
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
Apologies if this is too simple question and has been asked 100 times, But i can't seem to find the answer I'm looking for..
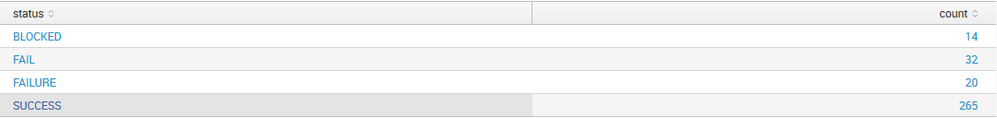
For the time being, I simply want to graph the number transaction status over time from a sourcetype which shows the following: "SUCCESS" "FAILED", "BLOCKED"...
However, for failed transactions, the data is coming in with failed status= "FAIL" or "FAILURE".
How can I make "FAILED = FAIL + FAILURE", and plot the status = SUCCESS & status = BLOCKED along side it?
I'm currently using the search:
sourcetype= mydata | stats count by status
As per below:
Cheers,
Craig
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this!
sourcetype= mydata|eval status=if(status="FAIL" OR status="FAILER","FAILED",status) | stats count by status
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Since Hiroshi beat me to it with eval, for completeness here is how you can do it with foreach
sourcetype= mydata
| stats count by status
| foreach status [eval <<FIELD>> = if((<<FIELD>>=="FAIL" OR <<FIELD>>=="FAILURE"),"FAILED",<<FIELD>>) ]
| stats sum(count) as count by status
See: http://docs.splunk.com/Documentation/Splunk/6.5.1/SearchReference/Foreach
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the reply mate.
Interested to investigate this method a little further,
When I run your command, it doesn't seem to return any results :s
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
interesting - it definately should!
Here's a run anywhere example:
|gentimes start=-1
| eval status="FAIL"
| stats count by status
| foreach status [eval <<FIELD>> = if((<<FIELD>>=="FAIL" OR <<FIELD>>=="FAILURE"),"FAILED",<<FIELD>>) ]
| stats sum(count) as count by status
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this!
sourcetype= mydata|eval status=if(status="FAIL" OR status="FAILER","FAILED",status) | stats count by status
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Beat me to it!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Awesome, thanks guys 🙂