- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Actions in regards to events coming in
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have searches for 4740 account lockouts not showing as action=lockout but instead as action=modified.
This is important to us as we are trying to configure ES but that's one dashboard where we aren't getting any results.
Where do we go to fix this?
Also whenever you get a a source or field that shows as "unknown" whats the best way to go about fixing these?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @domino30,
yes, calculated fields (like the one you shared) are one of the methods to normalize data.
Let me know if you solved your issue.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @domino30,
this job is called "normalization", in other words, you have to create some sules (using reneme and calculated fields) to align yur values with the waited ones.
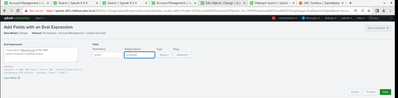
In your case, you have to add to your Add-On a custom calculated field like the following:
| eval action=if(EventCode=4740 AND action="lockout","modified",action)you can find more infos at https://lantern.splunk.com/Splunk_Platform/Product_Tips/Data_Management/Normalizing_values_to_a_comm... and at https://docs.splunk.com/Documentation/CIM/5.1.1/User/Overview
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Like this?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @domino30,
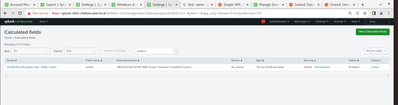
No, this is the possibility to add fields to a DataModel.
You have to create (usually in an Add-On) a calculated field [Settings > Fields > Calculated Fields] that makes the transformation BEFORE an event is added to a Datamodel.
In other words, the process is the following:
- events are tagged using eventtypes in the Add-Ons (for this reason, before using an Add-On check the CIM compliance or create a CIM compliant Add-On),
- fields are renamed in the Add-Ons to have the field names predefined for that Data Model,
- values are normalized using calculated fieds in the Add-Ons,
- the scheduled searches populate the Data Model adding all the fields already normalized.
for more infos see at https://docs.splunk.com/Documentation/CIM/5.1.1/User/Overview
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
like this? btw its working now just confirming something
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @domino30,
yes, calculated fields (like the one you shared) are one of the methods to normalize data.
Let me know if you solved your issue.
Ciao.
Giuseppe