Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- ASUS Router Query Super Thread
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ASUS Router Query Super Thread
Since I cannot find much on querying ASUS router syslogs, and I am completely new to Splunk, I thought I'd start a thread for other Google Travelers in the far future.
I installed Splunk ENT yesterday and I am successfully sending syslogs.
In my first self-challenge, I'm trying to build a query with just dropped packets for external IP sources, but its not working.
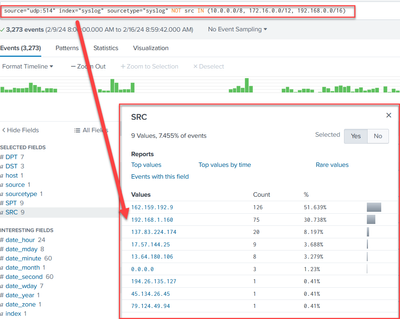
source="udp:514" index="syslog" sourcetype="syslog" | where !(cidrmatch("10.0.0.0/8", src) OR cidrmatch("192.168.0.0/16", src) OR cidrmatch("172.16.0.0/12", src))
The Raw data is below - I wanna filter out all 192 privates and just external addresses, like that darn external HP src IP (15.73.182.64).
Feb 4 08:46:36 kernel: DROP IN=eth4 OUT= MAC=04:42:1a:51:a7:70:f8:5b:3b:3b:bd:e8:08:00 src=15.73.182.64 DST=192.168.1.224 LEN=82 TOS=0x00 PREC=0x00 TTL=50 ID=43798 DF PROTO=TCP SPT=5222 DPT=24639 SEQ=120455851 ACK=2704633958 WINDOW=23 RES=0x00 ACK PSH URGP=0 OPT (0101080A1D135F84C3294ECB) MARK=0x8000000
Feb 4 08:46:37 kernel: DROP IN=eth4 OUT= MAC=04:42:1a:51:a7:70:f8:5b:3b:3b:bd:e8:08:00 src=15.73.182.64 DST=192.168.1.224 LEN=82 TOS=0x00 PREC=0x00 TTL=50 ID=43799 DF PROTO=TCP SPT=5222 DPT=24639 SEQ=120455851 ACK=2704633958 WINDOW=23 RES=0x00 ACK PSH URGP=0 OPT (0101080A1D136188C3294ECB) MARK=0x8000000
Feb 4 08:46:38 kernel: DROP IN=eth4 OUT= MAC=04:42:1a:51:a7:70:f8:5b:3b:3b:bd:e8:08:00 src=15.73.182.64 DST=192.168.1.224 LEN=82 TOS=0x00 PREC=0x00 TTL=50 ID=43800 DF PROTO=TCP SPT=5222 DPT=24639 SEQ=120455851 ACK=2704633958 WINDOW=23 RES=0x00 ACK PSH URGP=0 OPT (0101080A1D136590C3294ECB) MARK=0x8000000
Feb 4 08:46:40 kernel: DROP IN=eth4 OUT= MAC=04:42:1a:51:a7:70:f8:5b:3b:3b:bd:e8:08:00 src=15.73.182.64 DST=192.168.1.224 LEN=82 TOS=0x00 PREC=0x00 TTL=50 ID=43801 DF PROTO=TCP SPT=5222 DPT=24639 SEQ=120455851 ACK=2704633958 WINDOW=23 RES=0x00 ACK PSH URGP=0 OPT (0101080A1D136DA0C3294ECB) MARK=0x8000000
Feb 4 08:46:44 kernel: DROP IN=eth4 OUT= MAC=04:42:1a:51:a7:70:f8:5b:3b:3b:bd:e8:08:00 src=15.73.182.64 DST=192.168.1.224 LEN=82 TOS=0x00 PREC=0x00 TTL=49 ID=43802 DF PROTO=TCP SPT=5222 DPT=24639 SEQ=120455851 ACK=2704633958 WINDOW=23 RES=0x00 ACK PSH URGP=0 OPT (0101080A1D137DC0C3294ECB) MARK=0x8000000
Feb 4 08:46:52 kernel: DROP IN=eth4 OUT= MAC=04:42:1a:51:a7:70:f8:5b:3b:3b:bd:e8:08:00 src=15.73.182.64 DST=192.168.1.224 LEN=82 TOS=0x00 PREC=0x00 TTL=49 ID=43803 DF PROTO=TCP SPT=5222 DPT=24639 SEQ=120455851 ACK=2704633958 WINDOW=23 RES=0x00 ACK PSH URGP=0 OPT (0101080A1D139E00C3294ECB) MARK=0x8000000
Feb 4 08:47:09 kernel: DROP IN=eth4 OUT= MAC=04:42:1a:51:a7:70:f8:5b:3b:3b:bd:e8:08:00 src=15.73.182.64 DST=192.168.1.224 LEN=82 TOS=0x00 PREC=0x00 TTL=49 ID=43804 DF PROTO=TCP SPT=5222 DPT=24639 SEQ=120455851 ACK=2704633958 WINDOW=23 RES=0x00 ACK PSH URGP=0 OPT (0101080A1D13DE80C3294ECB) MARK=0x8000000
Feb 4 08:47:17 kernel: DROP IN=eth4 OUT= MAC=ff:ff:ff:ff:ff:ff:28:11:a8:58:a6:ab:08:00 src=192.168.1.109 DST=192.168.1.255 LEN=78 TOS=0x00 PREC=0x00 TTL=128 ID=41571 PROTO=UDP SPT=137 DPT=137 LEN=58 MARK=0x8000000
Next question - would anyone be able to write an app that takes the external IPs and does a lookup against the AbusePDB API or other blacklist APIs?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My two cents - most if not all small home routers use just linux kernel, some typical linux networking tools and custom WebUI. (Legality here is sometimes questionable).
So it's not "Asus router logs", it's just linux logs - in this case normal logs from the LOG module of iptables.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You were correct - I added linux_secure and now src_ip is happier than "src".
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Still having issues trying to exclude private IPs.
This works for individual IPs:
index="syslog" process="kernel" SRC!=192.168.1.160 SRC!=0.0.0.0
But still can't exclude blocks.
How can I exclude with wildcard the 192.x.x.x.?
Tried this -
source="udp:514" index="syslog" sourcetype="syslog" where not like(src, "%192%")
Nooby blues.
Google is not my friend today.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Still trying to figure this one out....
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Still trying to only get the Russian IPs. 🙂 Still pulls the private IPs. 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
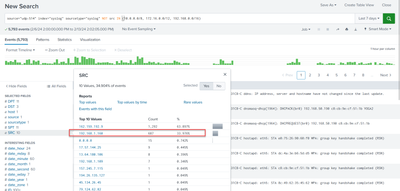
Thanks, that query is still returning private 192.168.x.x src IPs.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think there is no need where filter. you can find external ips in search filter. Can you try this ?
source="udp:514" index="syslog" sourcetype="syslog" NOT src IN (10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16)- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
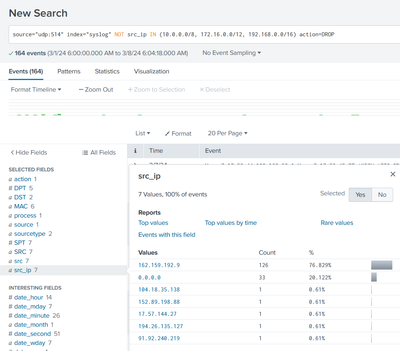
Got it working after adding src_ip field.
Splunk is a long journey to learning basic stuff 🙂
source="udp:514" index="syslog" NOT src_ip IN (10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16) action=DROP