- Find Answers
- :
- Premium Solutions
- :
- Splunk SOAR
- :
- How to have the "Run Playbook in Phantom" adaptive...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to have the "Run Playbook in Phantom" adaptive response to run a specific playbook?
Is it possible for the "Run Playbook in Phantom" adaptive response action in ES to automatically run a specific playbook instead of showing a popup window to manually select the playbook, Sensitivity, Severity and Label?
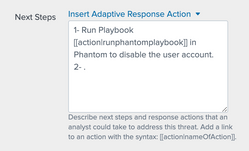
Specifically, I'm referring to the "Next Steps" box in the Notable adaptive response action, where I can include both text and additional adaptive response actions for the analyst to go thru.
See screenshot below for what I have currently. In the notable event that it generates, it turns into a link that give a popup of an empty Run Playbook box and I have to manually fill in the playbook, Severity, Sensitive and Label. Can I tweak the text inside the [[ ]] so it will pre-populated the playbook information?
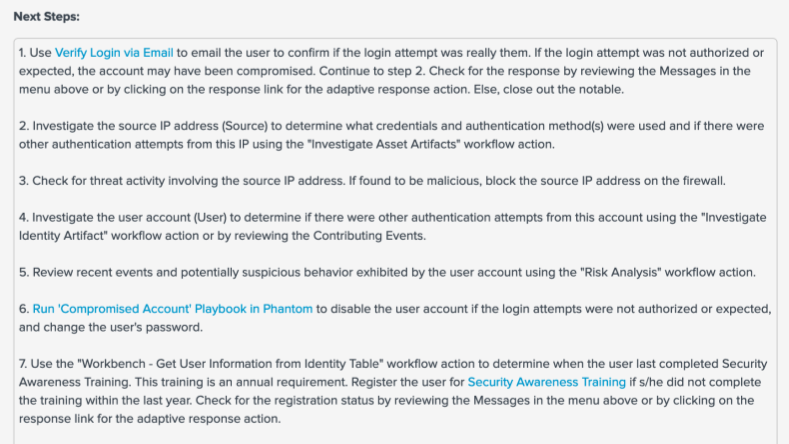
Ultimately I'm trying to replicate what I saw during BOTS where one of the notable events that we had to investigate had this really detailed "Next Steps" box (screenshot below). For step 6, the link will automatically call that "Compromised Account" playbook.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey,
Do you have a "Send to Phantom" adaptive response action? If yes, you can use that to automatically send a ES Notable to Phantom (which will then create a Phantom Container).
In addition, you must set a specific label in the ES Alert (e.g. malware, phishing, etc...) The label will be used as a trigger mechanism for a specific playbook to run.
Once you finish adding a label in the ES Notable alert, You must also add the label on the Splunk Phantom side (Under Administration > Events Settings > Label settings > (add your preferred label name in here) PS: Don't use spaces in the label name, instead, use underscore "_" (e.g. host_ips / network_ips)
Once you have done this, open the Phantom Playbook you want to run, Edit it, and under Playbook Settings > Operates on > select the preferred label you want to run.
Set "Active" to On so that when a new containers comes into phantom that matches the label you used, the Playbook will automatically be triggered. Save the playbook and trigger some alerts to test...
Hope this helps,
Carl