- Find Answers
- :
- Premium Solutions
- :
- Splunk ITSI
- :
- ITSI maintenance window capabilities for a non adm...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We need to allow a non admin user to be able to create, modify and delete maintenance windows from ITSI. We have try to add this capabilities to the user_role:
- read_maintenance_calendar
- write_maintenance_calendar
- delete_maintenance_calendar
And also making the maintenance window lister available to the role.

But we still can not create the maintenance window with the user.

Can you please help us to understand what is missing?
Regards,
Jemil Garcia
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To give the 'service' user permission to create, change and delete Maintenance Windows we had to make several changes to the files in ITSI.
1) Enable Maintenance Windows capabilities
First, in the 'authorize.conf' file we enabled the following capabilities for the 'service' user:
read-maintenance_calendar
write-maintenance_calendar
delete-maintenance_calendar
Documentation:
https://docs.splunk.com/Documentation/ITSI/4.3.0/Install/Capabilities
2) Make the Maintenance WIndow visible on the dashboard
The second step is to make the Maintenance Window visible to the 'service' user.In our case, the 'service' user should be able to access the Maintenance Window view but also be able to make changes. To do this we had to give the 'service' user read, write and delete permissions in the following ITSI views in the file 'local.meta':
[views/maintenance_windows_lister]
access = read : [ itoa_admin, itoa_team_admin, service ], write: [ itoa_admin, itoa_team_admin, service ], delete: [ itoa_admin, itoa_team_admin, service ]
[views/maintenance_window_detail_view]
access = read : [ itoa_admin, itoa_team_admin, itoa_user, service ], write: [ itoa_admin, itoa_team_admin, itoa_user, service ], delete: [ itoa_admin, itoa_team_admin, itoa_user, service ]
You can find (or should I say, you should create) this file ('local.meta') in the following folder:
/opt/splunk/etc/shcluster/apps/itsi/metadata/
3) Set permissions for the KV store collections
The next step is to set the permissions for the KV store collections. This can be done in the 'local.meta' file (if this file doesn't exist, create it and don't make changes to the 'default.meta' file) in the following directory:
/opt/splunk/etc/shcluster/apps/SA-ITOA/metadata/
The only change we made in this file is that we gave read, write and delete permissions to the 'service' user to the following collection:
[collections/maintenance_calendar]
access = read : [ itoa_admin, itoa_team_admin, itoa_analyst, itoa_user, service ], write: [ itoa_admin, itoa_team_admin, service ], delete: [ itoa_admin, itoa_team_admin ]
Documentation:
https://docs.splunk.com/Documentation/ITSI/4.3.0/Install/UsersandRoles#Set_permissions_to_KV_store_c...
4) Set shared Application-level permissions
Step is to set give the 'service' user write permissions to make changes to objects in shared applications. We made the change in the 'local.meta' file in the following directory:
/opt/splunk/etc/shcluster/apps/DA-ITSI-STORAGE/
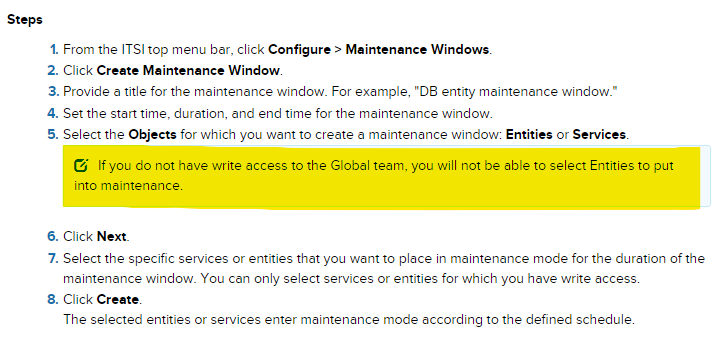
5) Change permissions in the Global team
The last step was to give the 'service' user permission to access the entities and services that belong to the Global team. Without this the 'service' user couldn't put any entities or services in Maintenance Mode.
You can find the file in the following directory:
Splunk/searchheads/itsi_configurations/import/itsi_team___team___0.json
Documentation:
https://docs.splunk.com/Documentation/ITSI/4.2.1/Configure/MaintenanceWindows
And that's how we made it possible for the 'service' user to create, change and delete Maintenance Windows 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To give the 'service' user permission to create, change and delete Maintenance Windows we had to make several changes to the files in ITSI.
1) Enable Maintenance Windows capabilities
First, in the 'authorize.conf' file we enabled the following capabilities for the 'service' user:
read-maintenance_calendar
write-maintenance_calendar
delete-maintenance_calendar
Documentation:
https://docs.splunk.com/Documentation/ITSI/4.3.0/Install/Capabilities
2) Make the Maintenance WIndow visible on the dashboard
The second step is to make the Maintenance Window visible to the 'service' user.In our case, the 'service' user should be able to access the Maintenance Window view but also be able to make changes. To do this we had to give the 'service' user read, write and delete permissions in the following ITSI views in the file 'local.meta':
[views/maintenance_windows_lister]
access = read : [ itoa_admin, itoa_team_admin, service ], write: [ itoa_admin, itoa_team_admin, service ], delete: [ itoa_admin, itoa_team_admin, service ]
[views/maintenance_window_detail_view]
access = read : [ itoa_admin, itoa_team_admin, itoa_user, service ], write: [ itoa_admin, itoa_team_admin, itoa_user, service ], delete: [ itoa_admin, itoa_team_admin, itoa_user, service ]
You can find (or should I say, you should create) this file ('local.meta') in the following folder:
/opt/splunk/etc/shcluster/apps/itsi/metadata/
3) Set permissions for the KV store collections
The next step is to set the permissions for the KV store collections. This can be done in the 'local.meta' file (if this file doesn't exist, create it and don't make changes to the 'default.meta' file) in the following directory:
/opt/splunk/etc/shcluster/apps/SA-ITOA/metadata/
The only change we made in this file is that we gave read, write and delete permissions to the 'service' user to the following collection:
[collections/maintenance_calendar]
access = read : [ itoa_admin, itoa_team_admin, itoa_analyst, itoa_user, service ], write: [ itoa_admin, itoa_team_admin, service ], delete: [ itoa_admin, itoa_team_admin ]
Documentation:
https://docs.splunk.com/Documentation/ITSI/4.3.0/Install/UsersandRoles#Set_permissions_to_KV_store_c...
4) Set shared Application-level permissions
Step is to set give the 'service' user write permissions to make changes to objects in shared applications. We made the change in the 'local.meta' file in the following directory:
/opt/splunk/etc/shcluster/apps/DA-ITSI-STORAGE/
5) Change permissions in the Global team
The last step was to give the 'service' user permission to access the entities and services that belong to the Global team. Without this the 'service' user couldn't put any entities or services in Maintenance Mode.
You can find the file in the following directory:
Splunk/searchheads/itsi_configurations/import/itsi_team___team___0.json
Documentation:
https://docs.splunk.com/Documentation/ITSI/4.2.1/Configure/MaintenanceWindows
And that's how we made it possible for the 'service' user to create, change and delete Maintenance Windows 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Splunk/searchheads/itsi_configurations/import/itsi_team___team___0.json
not able to find this path