Join the Conversation
- Find Answers
- :
- Premium Solutions
- :
- Splunk ITSI
- :
- ITSI episodes and notables have duplicate field va...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
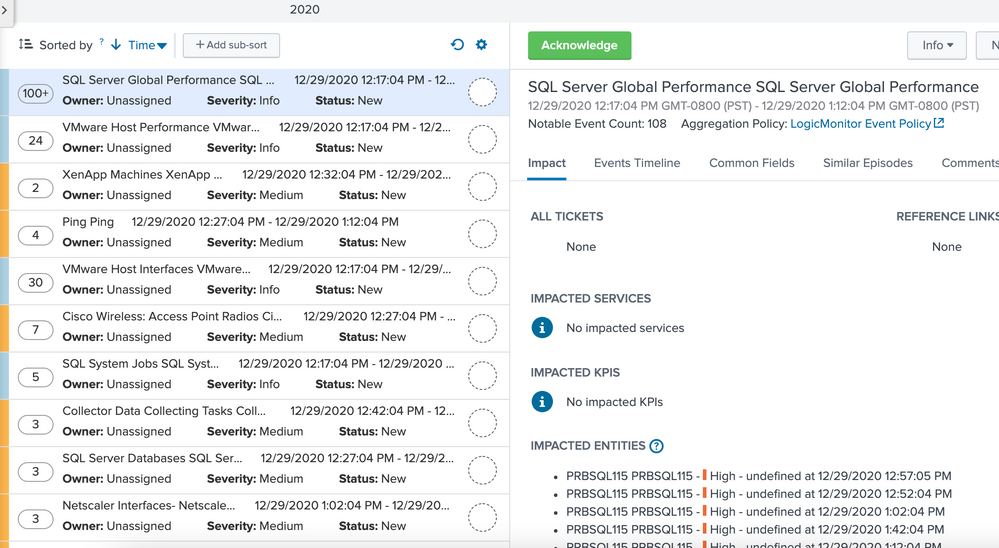
ITSI episodes and notables have duplicate field values (title, entity, identifier)
Hello Splunkers,
We have a new correlation search deployed to ingest a 3rd party (logicmonitor) system's alerts. The long/short is, we have a script polling their API every minute and writing the events in JSON to an index. Each alert is an individual event and they all have unique IDs.
The correlation search is super simple mapping severity and itsi_eventtype. The following details are configured in the search:
Entity Lookup Field = ObjectName
(this is a field with the name of the object creating the alert, this maps to entities in ITSI and usually a hostname or IP)
Notable Event Title = %TemplateName%
(this is the field in the data showing the common rule that's triggered and how we group the events)
Severity = %severity%
(mapped using eval)
We then have an aggregation policy which matches the itsi_eventtype which is created using eval and then splits the notables by TemplateName field.
Everything is working, execpt the episodes / notable titles are duplicated (e.g. SQL Performance Alert SQL Performance Alert. Where the TemplateName value would be "SQL Performance Alert"). This happens also for the impacted entities, event timeline event type, etc.)
Not sure what's going on here, it seems only to impact this one correlation search, the only other correlation search comes from the kubernetes content pack and it works fine.
Thanks for any help!!