Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Platform
- :
- Splunk Enterprise
- :
- Why is my case command with less than or equal to ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why is my case command with less than or equal to operator not categorizing correctly?
Hi All,
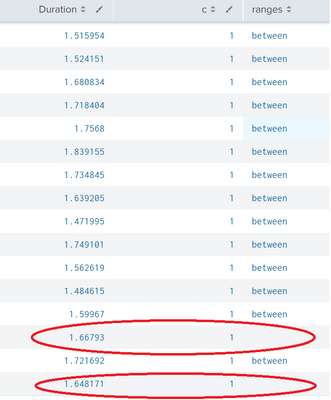
I have the below line of code to categorize transactions based on the response time (duration) taken in seconds.
| eval ranges=case(Duration<=1,"less",Duration>1 and Duration<=3,"between",Duration>3,"greater")Say i trigger a load test with 100 transactions which are all taking between 1 to 3 Secs but surprisingly few txns say 1 to 4 txns out of 100 are NOT getting categorized in the table though their duration column has a value between 1 to 3 Secs. Can someone please let me know what is going wrong.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Check if you're not having those values as strings. If so, you have to cast them to numbers by using tonumber().
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@PickleRick , Thank you very much, that gave me a clue and i tried the below line (WORKED) and it worked.
| eval ranges=case(Duration<="1", "less", Duration>"1" AND Duration<="3", "between", Duration>"3", "greater")
INSTEAD OF (NOT WORKING)
| eval ranges=case(Duration<=1,"less",Duration>1 and Duration<=3,"between",Duration>3,"greater")