Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Enterprise
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Splunk Platform
- :
- Splunk Enterprise
- :
- Splunk Stream: Dropping DNS events
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Splunk Stream: Dropping DNS events
a_kearney
Path Finder
11-29-2023
07:03 AM
Hi,
I am runing Splunk Stream to collect DNS data from Domain Controllers. On some of the busy DCs the Splunk_TA_stream is generating lots of the following errors:
ERROR [9412] (SplunkSenderModularInput.cpp:435) stream.SplunkSenderModularInput - Event queue overflow; dropping 10001 events
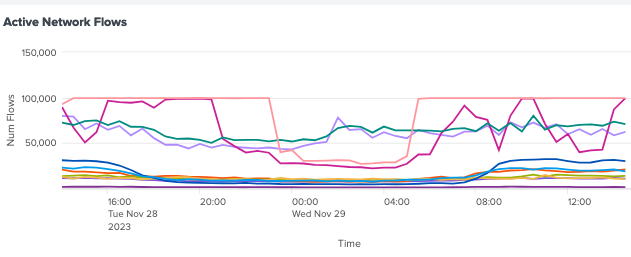
Looking at the Splunk Stream Admin-Network Metrics dashboard these seem to occur at the same the Active Network Flows seem to be hitting a limit:
I would like to increase the number of network flows allowed in an attempt to stop the event queue overflows. Looking at the documentation I can see 2 configurations that seem relevant:
maxTcpSessionCount = <integer> * Defines maximum number of concurrent TCP/UDP flows per processing thread.
processingThreads = <integer> * Defines number of threads to use for processing network traffic.
Questions:
1) What is the default for maxTcpSessionCount and processingThreads?
2) Would parameter would it be better to increase?
Also are these the correct parameters to be looking to tune with the errors I am getting. If not what should I look at?
Get Updates on the Splunk Community!
Automatic Discovery Part 1: What is Automatic Discovery in Splunk Observability Cloud ...
If you’ve ever deployed a new database cluster, spun up a caching layer, or added a load balancer, you know it ...
Real-Time Fraud Detection: How Splunk Dashboards Protect Financial Institutions
Financial fraud isn't slowing down. If anything, it's getting more sophisticated. Account takeovers, credit ...
Splunk + ThousandEyes: Correlate frontend, app, and network data to troubleshoot ...
Are you tired of troubleshooting delays caused by siloed frontend, application, and network data? We've got a ...