Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Platform
- :
- Splunk Enterprise
- :
- Index only events matching with pattern and exclud...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
In particular sourcetype we are getting huge numbers of events but only some data events are relevant. I am try to take only events with matching string and exclude everything else.
Matching strings : Session initialization | Session initialized (There are few more as well)
I have tried this by refereing this post Link
When I am using this its excluding everyting and when i tried only with setparsing its injesting all data. Not sure what I am missing here.
props.conf
[mx_java_event]
DATETIME_CONFIG =
LINE_BREAKER = ([\r\n]+)
NO_BINARY_CHECK = true
category = Custom
pulldown_type = true
EXTRACT-JavaClass = ,\d+\s\[(?<JavaClass>[^:]*):
EXTRACT-Session = session:(?<Session>\d+)
TRANSFORMS-set = setnull, setparsing
transforms.conf
[setnull]
REGEX = .
DEST_KEY = queue
FORMAT = nullQueue
[setparsing]
REGEX = Session initialization | Session initialized
DEST_KEY = queue
FORMAT = indexQueue
FYI : In case REGEX is incorrect, I tried with "REGEX = Session" its not working either.
Sample data: (Only 1st and 3rd line are matching)
2020-08-12 14:08:11,775 [Thread-233 - Worker-54] murex.processing.stp.osp.server.service.OspServer : DEBUG - [session:1758555252] Session initialization - SGITOPS/SG_LAW_MRC
2020-08-12 14:08:12,775 [Thread-233 - Worker-54] murex.processing.stp.osp.server.service.OspServer : DEBUG - [session:1758555252] Excluded - SGITOPS/SG_LAW_MRC
2020-08-12 14:08:11,912 [Thread-233 - Worker-54] murex.processing.stp.osp.server.service.OspServer : DEBUG - [session:1758555252] Session initialized
2020-08-12 14:08:12,912 [Thread-233 - Worker-54] murex.processing.stp.osp.server.service.OspServer : DEBUG - [session:1758555252] Session Excluded2
2020-08-12 14:08:12,912 JUST FOR Testing
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
props.conf
[mx_java_event]
TRANSFORMS-set = setnull, setparsingtransforms.conf
NOTE: if event contains "Session initialization" OR "Session initialized" anywhere then the event will be indexed others are ignored.
[setnull]
REGEX = .
DEST_KEY = queue
FORMAT = nullQueue
[setparsing]
REGEX = (Session initialization|Session initialized)
DEST_KEY = queue
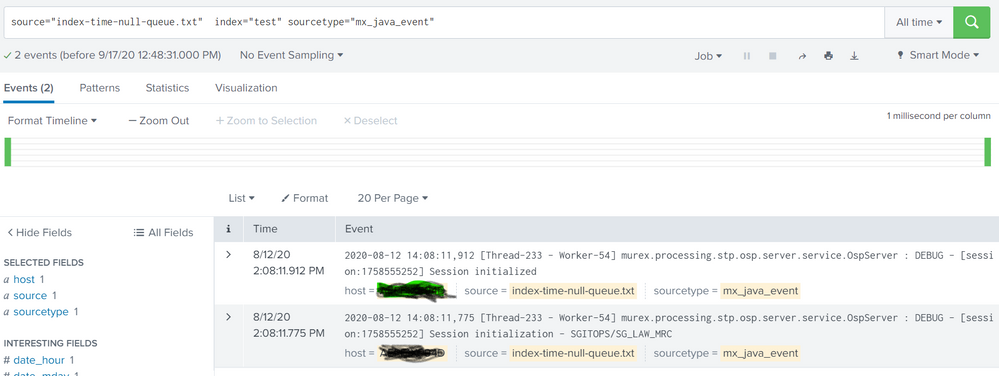
FORMAT = indexQueuebelow is output from your sample events:
If this helps, give a like below.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Provide sample events to test regex.
If this helps, give a like below.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
added sample data
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
props.conf
[mx_java_event]
TRANSFORMS-set = setnull, setparsingtransforms.conf
NOTE: if event contains "Session initialization" OR "Session initialized" anywhere then the event will be indexed others are ignored.
[setnull]
REGEX = .
DEST_KEY = queue
FORMAT = nullQueue
[setparsing]
REGEX = (Session initialization|Session initialized)
DEST_KEY = queue
FORMAT = indexQueuebelow is output from your sample events:
If this helps, give a like below.