Join the Conversation
- Find Answers
- :
- Splunk Platform
- :
- Splunk Enterprise
- :
- Field extraction to capture hostname
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Field extraction to capture hostname
Hi SMEs,
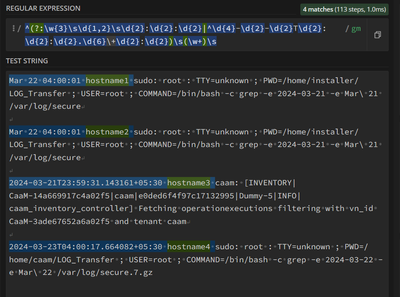
Seeking help on the below field extraction to capture hostname1, hostname2, hostname3 & hostname4
Mar 22 04:00:01 hostname1 sudo: root : TTY=unknown ; PWD=/home/installer/LOG_Transfer ; USER=root ; COMMAND=/bin/bash -c grep -e 2024-03-21 -e Mar\ 21 /var/log/secure
Mar 22 04:00:01 hostname2 sudo: root : TTY=unknown ; PWD=/home/installer/LOG_Transfer ; USER=root ; COMMAND=/bin/bash -c grep -e 2024-03-21 -e Mar\ 21 /var/log/secure
2024-03-21T23:59:31.143161+05:30 hostname3 caam: [INVENTORY|CaaM-14a669917c4a02f5|caam|e0ded6f4f97c17132995|Dummy-5|INFO|caam_inventory_controller] Fetching operationexecutions filtering with vn_id CaaM-3ade67652a6a02f5 and tenant caam
2024-03-23T04:00:17.664082+05:30 hostname4 sudo: root : TTY=unknown ; PWD=/home/caam/LOG_Transfer ; USER=root ; COMMAND=/bin/bash -c grep -e 2024-03-22 -e Mar\ 22 /var/log/secure.7.gz
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
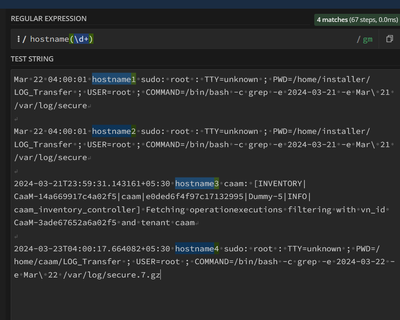
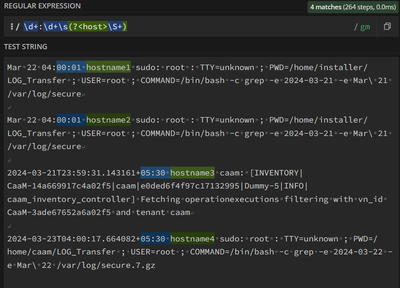
@pm2012Try this. We can do it in multiple ways.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content