Are you a member of the Splunk Community?
- Find Answers
- :
- Premium Solutions
- :
- Splunk Enterprise Security
- :
- Raw data on Enterprise Security
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Raw data on Enterprise Security
Hello guys! Does anyone know how I can get (raw data | raw log) from a dataset on Enterprise Security?
On Splunk Enterprise I usually use (| eval Log=_raw) and when I try to do the same on ES, I get empty response.
Thanks in advance for any help.
Cheers!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
By desfault, Splunk extracted field automatically,
You can use regex to extract data from Raw data:
| eval Log=_raw <your_regex>
or if you are not aware of regex you can select any row and extract from splunk UI. refer below image
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, you're right.
But for some reason I'm not receiving anything.
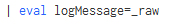
I define logMessage like below:
Then I use | table command and don't get anything.
Again, I don't know if Enterprise is different from Enterprise Security at this point.
Thanks again.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| rex field=_rawuse this... after _raw you need to add some regex:
https://docs.splunk.com/Documentation/SplunkCloud/8.2.2104/SearchReference/Rex