- Find Answers
- :
- Premium Solutions
- :
- Splunk Enterprise Security
- :
- PhishTank Threat Intelligence Not Writing to Colle...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am trying to enable the out of box PhishTank Threat Intelligence in ES. The file downloads correctly but it doesn't write to any KV store collection. From my understanding, it should write to one of the *_intel KV stores. What else do I need to configure?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks jawaharas,
I am not able to view the image you posted.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Avoid posting your response/query as new answer. Instead user 'Add Comment' option under corresponding post.
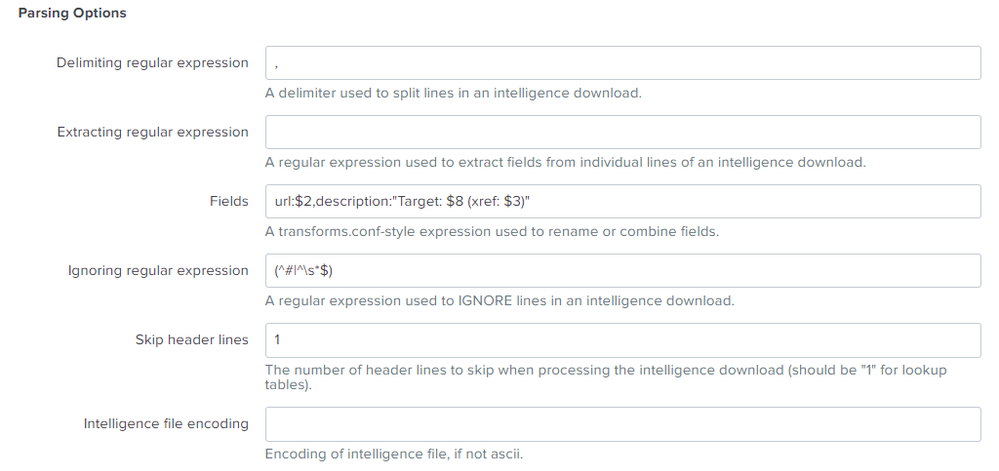
Text version of Parsing options:
Parsing Options-
Demiliting regular expression: ,
Extracting reguarl expression:
Fields: url:$2,description:"Target: $8 (xref: $3)"
Ignoring regular expression: (^#|^\s*$)
Skip header lines: 1
Intelligence file encoding:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@merzinger_prudent
Can you upvote and accept the answer if it's helped you? Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your help. That worked
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Parsing options for 'phishtank' intelligence downloads:
Can you accept the answer if it's helped you? Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your reply. I see the file being downloaded daily to$SPLUNK_BASE/etc/apps/SA-ThreatIntelligence/local/data/threat_intel/phishtank.csv, however the "threat_group_intel" lookup is empty. Could this be a parsing issue? What should the settings be for Parsing Options under Data Inputs>Intelligence Downloads>phishtank?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The 'phishttank' intel data is collected in 'threat_group_intel' kvstore collection.
You can verify the audit events to ensure the threat intelligences are collected by navigating to: Audit -> Threat Intelligence Audit in the ESS app menu.
Also, can you see data in '$SPLUNK_BASE/etc/apps/SA-ThreatIntelligence/local/data/threat_intel/phishtank.csv' file?