- Find Answers
- :
- Premium Solutions
- :
- Splunk Enterprise Security
- :
- How Do I Map Splunk Security Content to MITRE ATT&...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would like to map the Splunk Security Content from Enterprise Security (ES), Enterprise Security Content Update (ESCU), Splunk Security Essentials (SSE), and anything else to MITRE ATT&CK so that I can understand what content is available and data sources are available. Is there anything to help with that?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
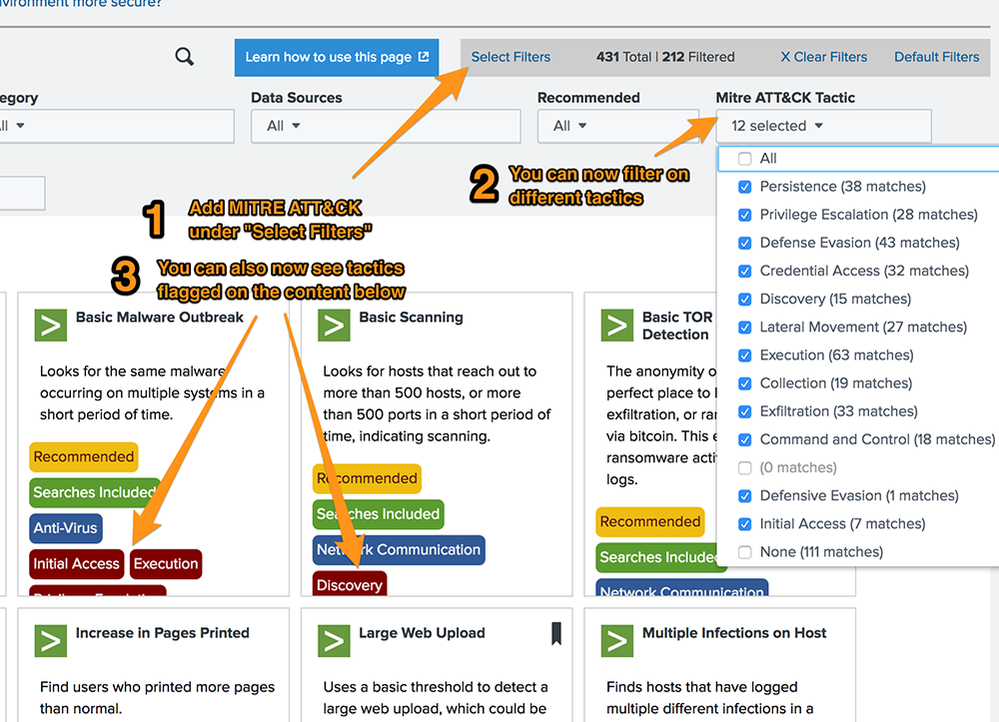
Very easily, in fact! In Splunk Security Essentials, all of the content from the Splunk ecosystem is listed including Splunk Security Content from Enterprise Security (ES), Enterprise Security Content Update (ESCU), Splunk Security Essentials (SSE), though there’s usually a bit of a delay with ESCU, since it’s released more often than Security Essentials. All of the content is mapped to MITRE ATT&CK tactics, and you can use that to visualize the data or filter to particular tactics you’re interested in.
To filter, go to the main Security Content page in the app. If you haven’t already added the ATT&CK Filter, click “Select Filters” in the gray box on the upper right-hand side, and toggle on the “MITRE ATT&CK Tactic.” You’ll now see this as a new filter option, and you’ll also see all of the content with MITRE applicability tagged in the main display!
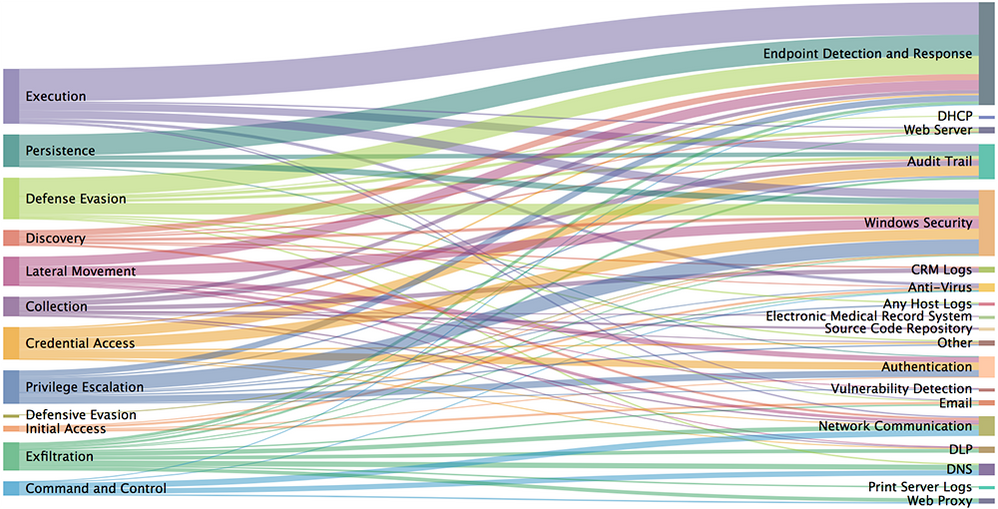
Splunk Security Essentials also includes some visualizations for data as well! In the next release (2.3.2), we’re adding a new panel to the Overview dashboard (hidden away in the Security Content menu) allowing you to visualize the relationships with a Sankey chart! Of course, you can adjust this analysis in any way you might want since it’s just SPL.
We’re looking for ways to enable a mapping at the Technique level as well in the future, so if you’re excited for that, stay tuned (or reach out here, or on Splunk Usergroups Slack @ davidveuve ). If you have any other suggestions for how to make this more usable for your needs, let us know!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is great and we are really looking forward to having this functionality in the next release and the ideals you have of mapping against Techniques sounds amazing.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Very easily, in fact! In Splunk Security Essentials, all of the content from the Splunk ecosystem is listed including Splunk Security Content from Enterprise Security (ES), Enterprise Security Content Update (ESCU), Splunk Security Essentials (SSE), though there’s usually a bit of a delay with ESCU, since it’s released more often than Security Essentials. All of the content is mapped to MITRE ATT&CK tactics, and you can use that to visualize the data or filter to particular tactics you’re interested in.
To filter, go to the main Security Content page in the app. If you haven’t already added the ATT&CK Filter, click “Select Filters” in the gray box on the upper right-hand side, and toggle on the “MITRE ATT&CK Tactic.” You’ll now see this as a new filter option, and you’ll also see all of the content with MITRE applicability tagged in the main display!
Splunk Security Essentials also includes some visualizations for data as well! In the next release (2.3.2), we’re adding a new panel to the Overview dashboard (hidden away in the Security Content menu) allowing you to visualize the relationships with a Sankey chart! Of course, you can adjust this analysis in any way you might want since it’s just SPL.
We’re looking for ways to enable a mapping at the Technique level as well in the future, so if you’re excited for that, stay tuned (or reach out here, or on Splunk Usergroups Slack @ davidveuve ). If you have any other suggestions for how to make this more usable for your needs, let us know!